Two-factor-authentication (2FA) is becoming an essential part of many organisations’ cybersecurity. 2FA actually blocks over 99.9% of account compromising attacks. It does this by adding an extra layer of defence against the rising number of cyberattacks by strengthening password security. Cybercrime is getting more sophisticated, so your level of cybersecurity should be doing the same. In this blogpost we’ll take you through what two-factor-authentication is and why you should consider implementing it in your organisation.
Short Summary:
- Two-factor authentication (2FA) is an important cybersecurity measure that blocks over 99.9% of account compromising attacks.
- 2FA protects accounts from unauthorized access that could occur due to weak passwords, password reuse, or password exposure through data leaks.
- By adding an extra step to the log-in process, implementing 2FA is a simple way to enhance the security of any account.
The rise in cybercrime
We’ve talked about it before, and we’ll talk about it again. Cybercrime is on the rise, and it’s expected to continually rise over the years and get more advanced. It only takes one human error to let the hackers through. Your organisation might have the best anti-virus software and firewall, but it’s also important to have the best human firewalls. People tend to make weak passwords or re-use them. Of course, we need to educate people in making strong passwords, but you should also consider adding two-factor-authentication to your cybersecurity repertoire to strengthen your defence.
What is two-factor-authentication?
Multi-factor-authentication, or two-factor-authentication as it’s also called, is a way of increasing the security level of your online accounts, by adding an extra layer of protection, aside from your username and password.
2FA is one of the best ways to protect your online account, as it adds another step and identification before you can log in. An example of an extra step of security could be a SMS with a 5-digit code besides your usual login information. It strengthens your security and makes it more difficult for intruders to get unauthorised access to your account.
Why passwords are not enough
You’re probably wondering why you should use two-factor-authentication, if you already have a strong password. The truth is that a password might not be enough to protect your account[s]. We often see data leaks from big organisations where your strong password can be made publicly available. You can check out the website HaveIBeenPwned, in order to see if your login information has been involved in a leak. You can also send the website to your co-workers to see if it has happened to them.
If you’re working in an organisation, you can’t be sure that all your co-workers have strong passwords. Here are some common mistakes that people make when creating their passwords.
Reused passwords
We are lazy creatures and most of us probably have one password that we reuse for multiple accounts. This makes sense since it’s impossible to remember 50 different passwords. You might even have used the same password for both personal and work accounts. In this case, if your passwords get leaked somehow, you’ve put your organisation in danger.

Too common passwords
Many people still use very common passwords, such as “123456”, “Password”, “123123” and so on. These are some of the most used passwords on the internet, and all of these take a hacker less than one second to crack.
Passwords that are too short/simple
Many people use simple passwords, that are easy to remember. A lot of people do this, because it is easier than having to remember many long passwords. Many people also have the idea that it won’t happen to them, when it comes to hacking.
We’ve made a guide on how you can make a strong password that you can remember, if you want to avoid some of these typical password mistakes.
Why use two-factor authentication?
Two-factor-authentication has an important role in strengthening your organisation’s security, as it can block several attacks aimed at your organisation.
No matter how your co-worker's password might get hacked, two-factor-authentication can protect your company. By adding 2FA to your organisation you significantly improve your cybersecurity, as 2FA can save you from several phishing attacks. Here’s an example where the use of 2FA can protect you from a potential attack.
A co-worker falls victim to a phishing email
One of your co-workers falls victim to a phishing email where they share their credentials with a cybercriminal. The cybercriminal then tries to log onto the co-worker’s account but is unable to enter the authorization code sent to the co-worker's phone. The co-worker also gets an alert, that someone is trying to log in to their account, who isn’t them.
Here the 2FA stopped a phishing attack that could have caused severe damage. The co-worker should alert the IT department as well as be aware of potential phishing attacks in the future.
How secure is 2FA
A 2019 report from Microsoft concluded that 2FA can block over 99.9 percent of account compromising attacks. With 2FA, even if a cybercriminal cracks your password, it won't be enough to gain access to your account. That’s a great reason to consider implementing two-factor-authentication in your company.
The different types of 2FA
There are a bunch of different two-factor-authentication methods out there. We’ve compiled some of the most common ones here.
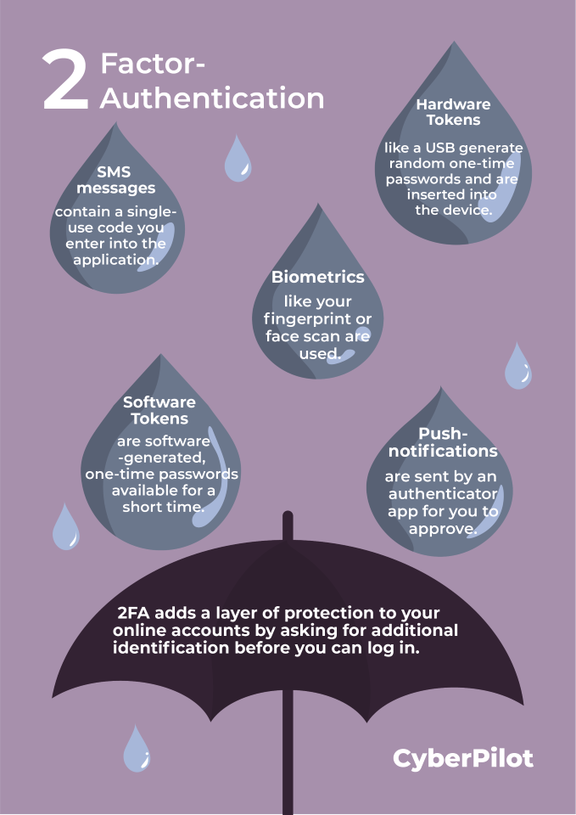
SMS text message
This kind of 2FA was used in the example above and is very simple. Here you just make a request on the website or program you’re trying to log on to, and you receive a text message sent to you with a single-use code, that you have to enter into the application. From there you have access to the application.
Push-Notifications
To get push-notifications, you have to download an authenticator app. There are many kinds of authenticator apps that fit to each program, and Microsoft and Google e.g., have their own ones. Instead of getting a text message with a single-use code, you get a notification on your phone that you just tap, in order to approve the request.
Biometrics
Biometrics are where you are the authenticator! A biometric authenticator could be any of your personal characteristics. The most common ones are facial recognition and fingerprint reader, which you probably know of from your smartphone.
Software tokens
Software tokens are software-generated, time-based, one-time passwords (TOTP). They are a popular form of two-factor-authentication, since the passwords only last for about a minute before they pass. In order to use this kind of authentication, you need to install a 2FA app. This kind of 2FA is very secure since the TOTP only lasts for a minute before a new one is automatically generated.
Hardware tokens
Hardware tokens are a type of two-factor-authentication, where you need a physical object to access, e.g., a computer. They usually come in the form of a USB flash drive, which generates random one-time-passwords (OTP). Here you have to physically insert the USB dongle, in order to authenticate your credentials and log onto your computer or application.
Which sort of authentication service best fits your needs, depends on your organisation. The most widely used methods are text messages and push notifications, which are fine for most organisations.
How to set up two-factor-authentication
Two-factor-authentication is very commonplace, and a lot of organisations support it. For example, Google offers it for all their services. Microsoft also supports a wide variety of authentication options, both for their free services, as well as Microsoft enterprise and business services, such as Office 365 and Microsoft 365.
You can set up an authenticator for these services by downloading the corresponding authenticator app on your smartphone and following the instructions. Social media like Twitter, Facebook and so on also support 2FA, which you can enable on your account.
Improving your organisation’s security culture with 2FA
By enabling two-factor-authentication in your organisation, you’ll significantly improve your level of security. Adding a 2FA initiative should be a main security objective, regardless of your organisation’s size. It’s one of the simplest and easiest ways to keep all yours accounts protected.
Adding two-factor-authentication throughout your whole organisation is a great way to improve the security culture, by making your co-workers aware of the benefits of having 2FA. Well-informed and aware employees can act as an additional line of defence in your organisation.
Adding two-factor-authentication is also a great way to show your customers that you take cyber security seriously. Stronger cyber security helps you to remain competitive in a world where the safety of your customers’ personal data is becoming more of a selling point.
To finish off, we'll give you probably the best description of what two-factor authentication is if you have to explain it to someone.
What is the best description of two-factor authentication?
So, if you ever have to describe two-factor authentication to someone. We'll say that the best way to describe two-factor authentication is probably like having two locks on your treasure chest to keep it safe.
- The First lock is your password (remember to make it strong). But instead of just relying on your password, which could potentially be guessed by someone else, you add an extra layer of protection.
- The Second lock could be a fingerprint scanner or a special key, that you add to the chest. This is your second lock on your treasure chest.
So now, in order to open the treasure chest, you need two things: the password (the first lock) and the fingerprint or the key (the second lock).
We hope you learned something useful about 2FA. If you have any questions feel free to reach out to us.

