Phishing emails are becoming more difficult to detect as cybercriminals are getting better at making their emails look real. Many of the traditional phishing email signals that we’ve been trained to detect, such as bad grammar or spelling mistakes, are showing up less frequently now. What this means is that we have to be more diligent so that we don’t fall victim to phishing scams. In this blog post, we identify some of the more complex signs of phishing emails. You can use these signs to look out for phishing emails in your inbox and share them with your entire team to strengthen your cybersecurity culture.
Detecting phishing emails protects you and your organisation
Since phishing is one of the biggest cybersecurity threats companies face today, it’s important that everyone can detect phishing emails in their inboxes. Everyone receives a phishing email at some point, so you can also share these tips with the rest of your organisation to strengthen your company’s resilience to phishing attacks. In the following sections, we’ll highlight a few signals in phishing emails so you and your entire organisation can sharpen your detection skills.
Phishing is becoming harder to detect
Unfortunately, it’s not always so easy to spot a phishing email. Phishing emails and the cybercriminals who create them have improved over the years. This means that phishing emails are becoming more convincing and less obvious, so it's more important than ever for you and the rest of your organisation to be careful.
Technology is the phisher’s best friend
We all love spell-check, but we have to remember that cybercriminals have access to the same spell-check software that we use in our emails. Therefore, their techniques are becoming more sophisticated and spotting spelling errors is not enough to keep us safe anymore.
In addition to spell-check, cybercriminals today have access to more software than ever before that they can use to make their phishing campaigns look real. For example, the dark web has phishing kits, which give malicious actors all the tools they need to create fake webpages that mimic the webpage of a legitimate company. If you visit one of these hacker-designed webpages, you won’t know that you have done anything wrong until you’ve entered sensitive data and it’s too late. AI tools like ChatGPT also make phishing easier than ever, because they can write phishing email templates for cybercriminals.
General phishing signals: when to exercise additional caution
Before getting into the more technical phishing signals, let’s start with the basic signs of a phishing email. Chances are that you and your team have probably heard of these phishing signs before, but they’re worth repeating because they form the foundation of most phishing emails. If you receive an email that fits these criteria, it could be a phishing email and it’s worth investigating the email further with our more technical tips that follow.
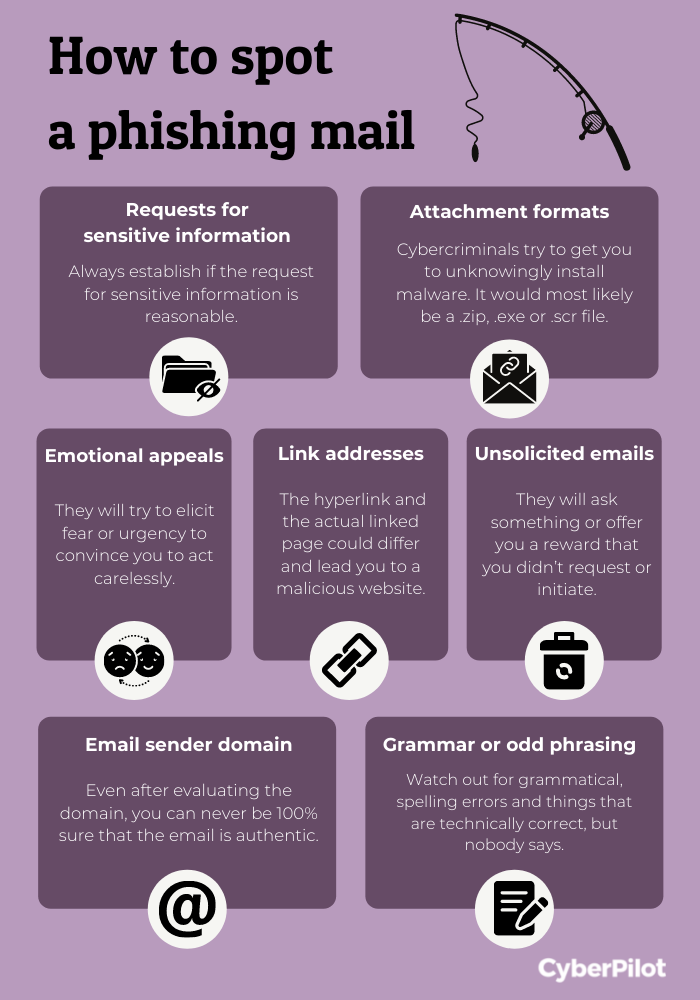
Unsolicited emails
A good practice is to keep your guard up when online, especially any time you receive an unsolicited email. That’s because phishing emails will usually ask you to do something or offer you a reward that you didn’t request or initiate yourself. If you receive an unsolicited email, this is the first indication that you should apply discretion.
Emotional appeals
Successful phishing emails will usually try to elicit feelings of fear or urgency within you to convince you to act without giving it a second thought. For example, emails that claim “embarrassing photos of you” or an “overdue balance” are designed to appeal to your instincts and promote an emotional response. Cybercriminals usually try to manipulate us by targeting the same emotions, such as:
-
Urgency
-
Desire to help others
-
Fear
-
Curiosity
-
Greed
-
Trust
-
Joy
If you receive an email that gives you an emotional rush, take a step back and look into it a bit further before immediately taking action.
Requests for sensitive information
To be successful, cybercriminals have to get something from you. In many cases, they will request your sensitive information in a phishing email. Any time an email requests sensitive information, such as information about a bank account, credit card number, or login credentials, you should take caution. Ask yourself: Do you know the sender of the email? Why do they need this information? What will they do with it once they have it? Do they really need it right now?
Bad grammar or odd phrasing
Yes, we know that spelling and grammar mistakes are becoming less and less common in phishing emails. But sometimes they still show up, and when they do, it could be a sign of phishing. Aside from grammatical and spelling errors, you can also look for odd phrasing – things that are technically correct and would pass the spelling and grammar check, but that people don’t often actually say. For example, a greeting like “Good Day, Madam” is technically correct, but when was the last time somebody you know wrote that in an email? Phrasing that is too formal or informal could be a sign of a phishing email.
Technical phishing signals to look out for and what to do about them
The phishing signs we’ve mentioned so far are some of the basic signs that you’ll see in many phishing emails. However, now that phishing techniques are becoming more sophisticated, you have to be more technical when you evaluate the authenticity of an email. Below are a few technical things to look out for in emails, as they could indicate that an email is a phishing attempt. These tips are easy for you to apply on your own and taking a few minutes to share them with your team can prevent your organisation from becoming a victim of phishing.
Email sender domain
This is the email address that the email comes from. A domain is different from the sender's name, which is what you typically see when you receive an email. Both the sender's name and the domain can easily be changed to try to trick recipients into believing it’s a real email.
For example, the sender's name could be “Facebook” and the email address could be “info@facebookmail.com.” At first glance, the email looks like it could be from Facebook, but a quick Google search of the domain name @facebookmail.com could tell you that it’s a fake domain. Also, if an email looks like it comes from a company but uses a generic domain such as @gmail.com or @outlook.com, it could be malicious.
Looking at the domain is important but, even after carefully evaluating the email domain, you can never be 100% sure that the email is authentic. This is because it is possible for cybercriminals to spoof emails if they take the time to do so. This is rare, though, because it takes some time and it’s a step that cybercriminals currently don’t need to take in order to succeed. However, it's something that could become more common in the future as phishing attacks continue to become more sophisticated.
Link addresses
Like the sender domain, there is a difference between what you first see and what is underlying. In this case, the text that is hyperlinked and the actual linked web address could be different.
For example, the text linked could show https://www.facebook.com, but the link that is associated with the text could be different and bring you to a website created by the hacker to steal your information. It is easy for anyone to change the text that is linked and the link address that it directs you to.
Before clicking on any link, hover over it with your mouse. This will reveal the linked website, so you can make sure the website is legitimate. If the linked website looks suspicious, you should be cautious with the email as it could be an indication of phishing. You have to be careful here because cybercriminals can create fake websites that mimic real ones. If you’re in doubt, you can always visit the trusted webpage by typing the address into your browser, rather than clicking the link in your email.

Attachment formats
Any time you’re sent an email with an unsolicited attachment, you should be cautious. Cybercriminals use discreet email attachments to get you to unknowingly install malware onto your computer. The attachment could be named something that seems important or benign, such as “Additional Information,” “Payment Receipt,” or “History of Use.” You should look for attachments that are commonly associated with malware downloads, such as .zip, .exe, and .scr.
Cybercriminals also hide malware in document formats that you’re used to using at work, such as Microsoft Word, Excel, and PDF documents. This is all the more reason to beware of unexpected attachments and carefully review unsolicited attachments before opening them. If you receive an unexpected attachment, don’t open it until you can verify the email’s legitimacy.
Be aware of both internal and external emails
Sometimes phishing emails will come from what looks like an external sender. For example, cybercriminals imitate big companies like Facebook, Microsoft, and Apple to try to get your attention - maybe these emails are asking you to verify your account information or reset your password.
But, a new kind of phishing, called spear phishing, is also something you should look out for. In these attacks, a cybercriminal impersonates somebody within your organisation. As you can imagine, these kinds of attacks are really dangerous, since we tend to trust emails from internal or known senders. Data from our own phishing campaigns reveals that taking advantage of company authority is the easiest way for cybercriminals to trick employees in phishing emails.
If you receive an unexpected request from somebody within your organisation, specifically in cases where you are asked to install software, update your credentials, or share banking information, you should confirm that the email is actually from that individual. Give them a call, text them, or stop by their desk to speak with them. Just make sure you don’t respond to the email asking if it’s them, since that will just put you in contact with the potential cybercriminal. Organisational awareness is key to protecting your team against spear phishing attacks.
You think you have been sent a phishing email. Now what?
If you suspect you have been sent a phishing email, you should follow your office’s process for reporting suspicious emails. If you’re an IT manager within your office, it’s important to have a clear reporting process that your organisation is aware of, so that your team knows what to do when they receive a suspicious email. Remember that recognising the signs of a phishing email is only part of the equation here, and that your team has to know what to do with a phishing email to best protect your company.
If the email is from an external sender
If the email is from an internal sender
-
Get in touch with the sender. As mentioned before, you can call them, text them, or talk to them in person to verify that they sent you the email. Just don’t email them, in case their email account has been compromised.
-
If your colleague confirms that the email is legitimate, you’re all good! If you cannot contact your colleague, or they confirm that the email was not actually from them, it’s time to notify your IT team and follow your company’s reporting policy.
Leave the email alone
Reporting the email is important, but it’s only part of how you should react to an attempted phishing attack. The best thing you can do is avoid interacting with the email, since opening attachments could lead you to unintentionally install malware onto your computer. We recommend deleting the email so that it’s no longer in your inbox.
If you made a mistake and already opened a suspicious email attachment from a suspected phishing email, you should tell your IT team.
Train your staff to recognize phishing attempts
Employees should know how to detect phishing emails and why they are dangerous
Phishing attacks become successful when even one employee mistakenly falls for the email. Most cyber-attacks begin with phishing emails, which makes human error a huge risk to IT security. To keep your organisation secure, it’s necessary for the entire team to understand the severity of phishing attacks and how to detect phishing emails. The good news is that it’s possible to train people to recognize and react appropriately to phishing attacks. You can share the detection tips in this blog post with your team to heighten their email awareness.
Put detection skills to test with real-life phishing simulations
Knowing how to detect a phishing email in theory is one thing, but actually catching one in your inbox can be tricky – especially since phishers are getting more sophisticated. Phishing simulations give your team the opportunity to practice their detection skills in real time, with “real” emails. Doing this testing continuously keeps your organisation sharp and clued into the newest phishing tactics out there.
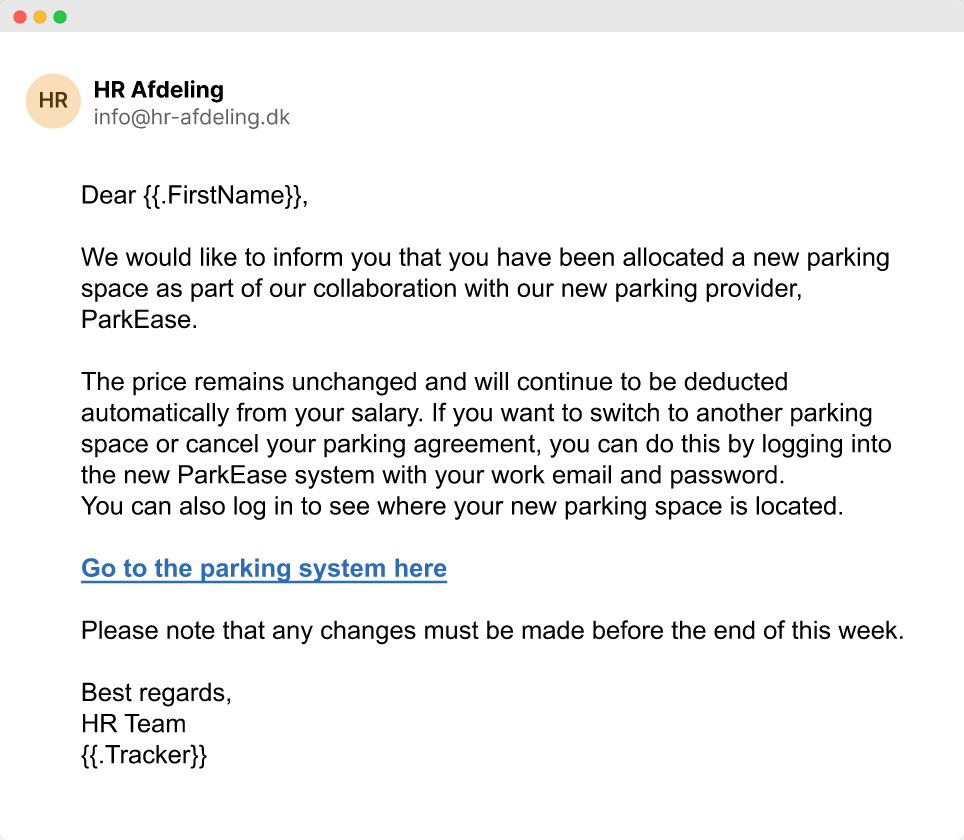
(This is an example of how a simulated phishing email could look like with our phishing training)
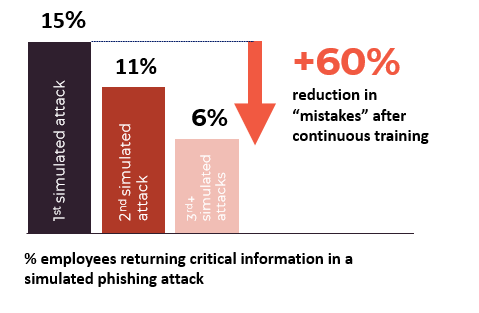
With our Phishing Training, you can teach your organisation to recognize phishing emails in their own inboxes. Our research shows that continuous awareness training and phishing training work! For example, after continuous awareness training and phishing testing, our users had over a 50% reduction in mistakes made during a phishing simulation.
We know that an aware team is a resilient team and training your team to become stewards of good IT security does not have to be a complicated process. If you are interested in learning more about phishing training and how you can implement it in your organisation, please don’t hesitate to reach out to us.

