We have a lot of data about how people react to different types of phishing campaigns – and we’ve decided to share it with you! In this blog post, we look at 12 phishing campaigns we’ve sent to many of our customers over the years. We break down the data to show you what kinds of phishing emails are the most dangerous and why, all through the lens of different social engineering techniques. You’ll see why we all need to be aware of phishing emails “from within” and the importance of knowing the signs of phishing emails. It’s not all doom and gloom though! Knowledge is power, and that’s certainly the case with phishing. So, you can use the lessons from our phishing data to focus your phishing training and improve your organization’s phishing preparedness.
We’ve sent 100,000 phishing emails. Here’s what you need to know
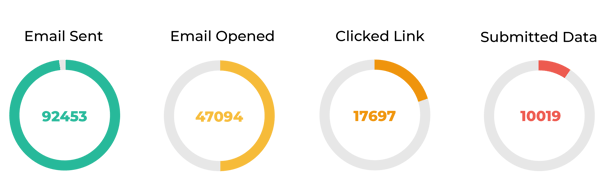
- An average of 10% of all recipients “fall through the trap” meaning they submit data
- Not all social engineering techniques are created the same. Taking advantage of company authority is the easiest way to trick employees
- Deadlines or urgency increase the data submission rate by 60%, so it’s important to always think twice
- The lure of a gift, reward, or benefit tricks many people into giving away their information
- It’s important to know the signs of a phishing email (and take the time to look for them)
These are just some of the findings our phishing campaign data reveal. So, let’s get into it!
The data comes from 12 different phishing campaigns
We’ve been sending phishing tests to our customers for years to help their organizations learn to detect malicious emails. To give you concrete insights into our treasure trove of phishing data, we looked at how 12 of our phishing campaigns performed on average. Our data can tell you exactly what makes a phishing email succeed.
Before we get into the data, you should know how our phishing campaigns work. Our phishing experts design fake phishing emails that use all the same tricks that actual cybercriminals use to get people to click and return their data. Social engineering is what makes phishing emails work, so we looked into how different social engineering techniques performed across the 12 campaigns.
Phishing emails rely on social engineering
The reason phishing emails work comes down to cybercriminals’ ability to take advantage of psychology and human weaknesses. This is called social engineering. According to IBM, “Social engineering manipulates people into sharing information they shouldn’t share, downloading software they shouldn’t download, visiting websites they shouldn’t visit, sending money to criminals, or making other mistakes that compromise their personal or organizational assets or security.”
Essentially, social engineering manipulates people instead of technology. That’s why phishing testing is so important. Because of how susceptible we are to social engineering, we become hackers’ easiest targets. We’ve written a full guide on how to get started with phishing testing in your organization if it’s something you’re curious to learn about.
Some social engineering techniques are more successful than others
Social engineering can include a lot of things, like taking advantage of the human desire to help others, succeed at work, receive gifts, or impress figures of authority. The social engineering techniques we measured in these 12 phishing campaigns include exploiting:
- The authority of the person’s own company or organization - 4 out of 12 campaigns
- The recipient’s desire for a gift, benefit, or reward - 4 out of 12 campaigns
- The tendency to react quickly or without thinking, in both routine and abnormal situations - 4 out of 12 campaigns
- The willingness to cooperate with external senders who ask for help – 1 out of 12 campaigns
- Human curiosity – 2 out of 12 campaigns
- Urgency created by short deadlines – 9 out of 12 campaigns
Here’s a quick overview of how well the different social engineering techniques worked based on how many people opened, clicked, and submitted data.
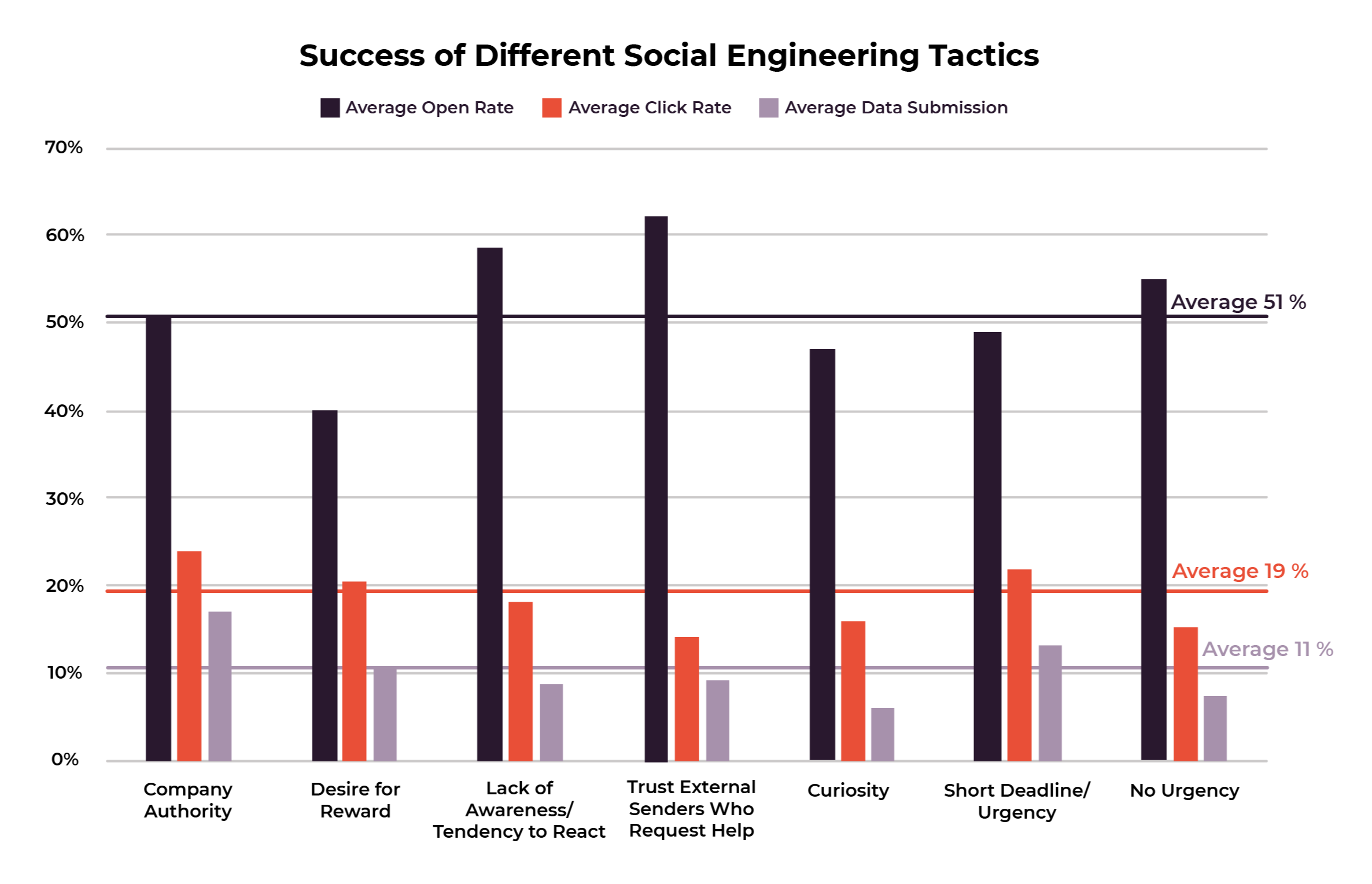
We'll get into the three techniques that worked the best in the next couple of sections: company authority, deadlines, and desire for rewards.
1st best performing social engineering technique: Company authority
Our data shows that phishing emails that take advantage of a company’s authority are the most successful. These kinds of emails had the most link clicks and data submitted. We sent four campaigns that appeared to come from within the recipients’ trusted company and on average, 24% of recipients clicked the link and 17% submitted their data.
To put this in perspective, for all the emails in this study, the average click rate was 19% and the average data submission rate was 11%. We’ve summarized the data here for you:
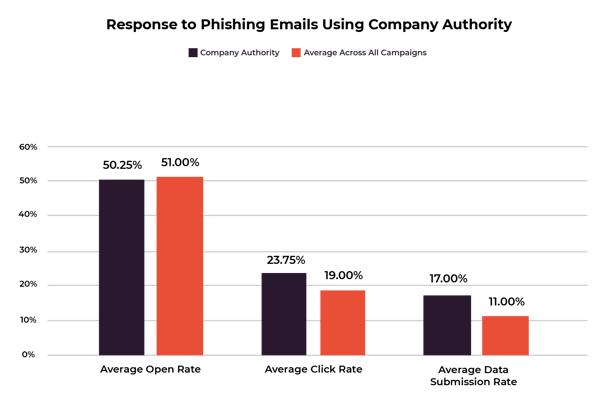
Because people tend to trust the emails they receive from their “company,” they are much more likely to trust these phishing emails. It’s great news for hackers because exploiting company authority increases the average number of people who submit their data by 40%.
The two most successful phishing campaigns in this category were emails about an emergency evacuation plan and a new password policy. These seem like typical emails one might receive from their company. It’s no surprise people had their guards down.
2nd best performing social engineering technique: Deadlines and urgency
The second most successful social engineering technique was the use of a short deadline. In the phishing campaigns that pushed a short deadline to act, more people clicked the links and submitted their data. The sense of urgency led 13% of recipients to submit their data and 22% to click the link.
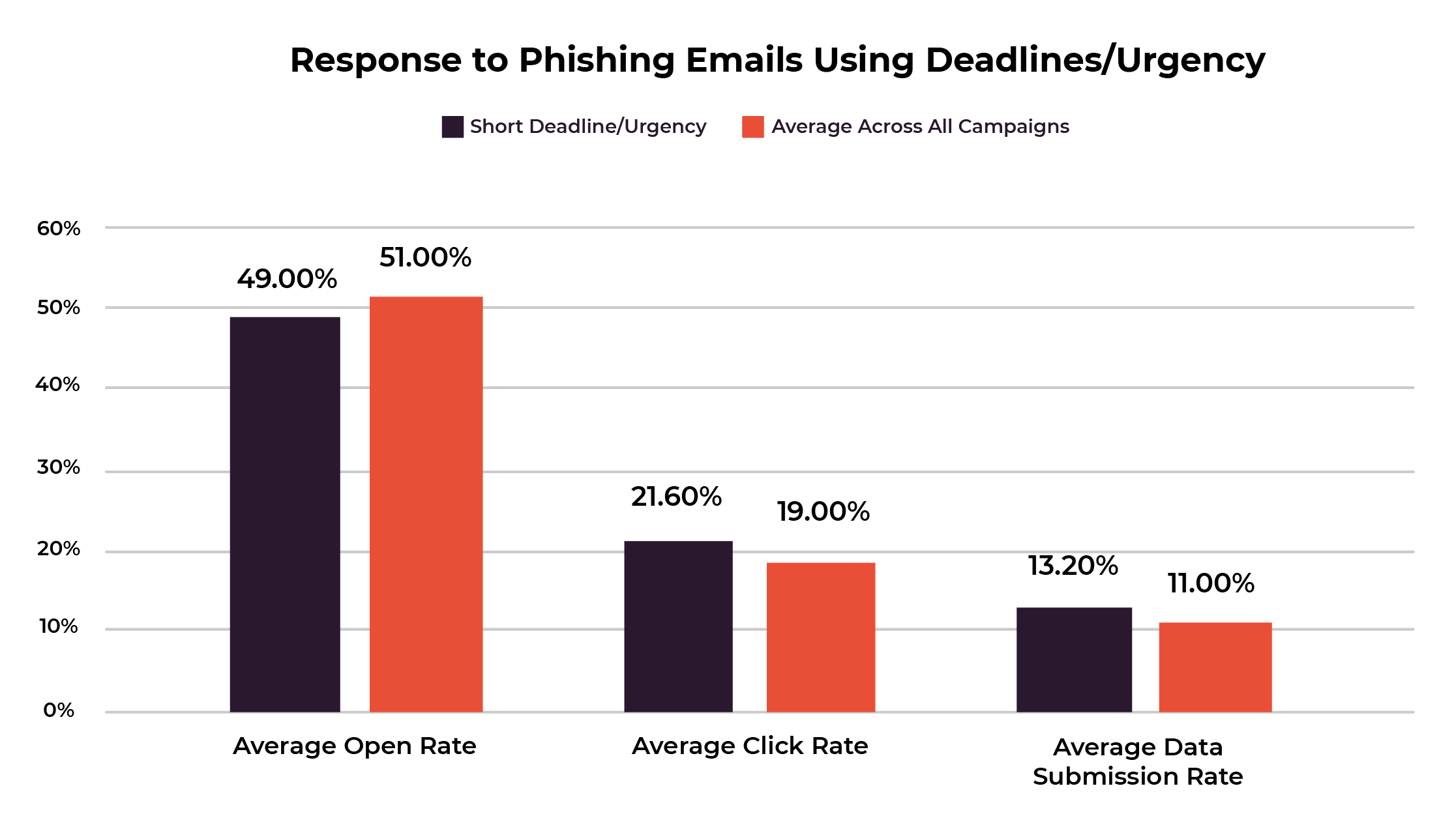 Most of the phishing campaigns we’re evaluating in this study featured a deadline to create a false sense of urgency. Deadlines are also something we’re used to seeing, since they help us set expectations and prioritize tasks at work. Our familiarity with deadlines and the stress they put on us to act quickly make them a successful social engineering technique.
Most of the phishing campaigns we’re evaluating in this study featured a deadline to create a false sense of urgency. Deadlines are also something we’re used to seeing, since they help us set expectations and prioritize tasks at work. Our familiarity with deadlines and the stress they put on us to act quickly make them a successful social engineering technique.
3rd best performing social engineering technique: Desire for gifts, rewards and benefits
This one probably won’t catch you by surprise. The third most successful social engineering technique was promising a reward or gift. These emails also had high click and data submission rates – on average, 21% of recipients clicked the link and 11% submitted their data.
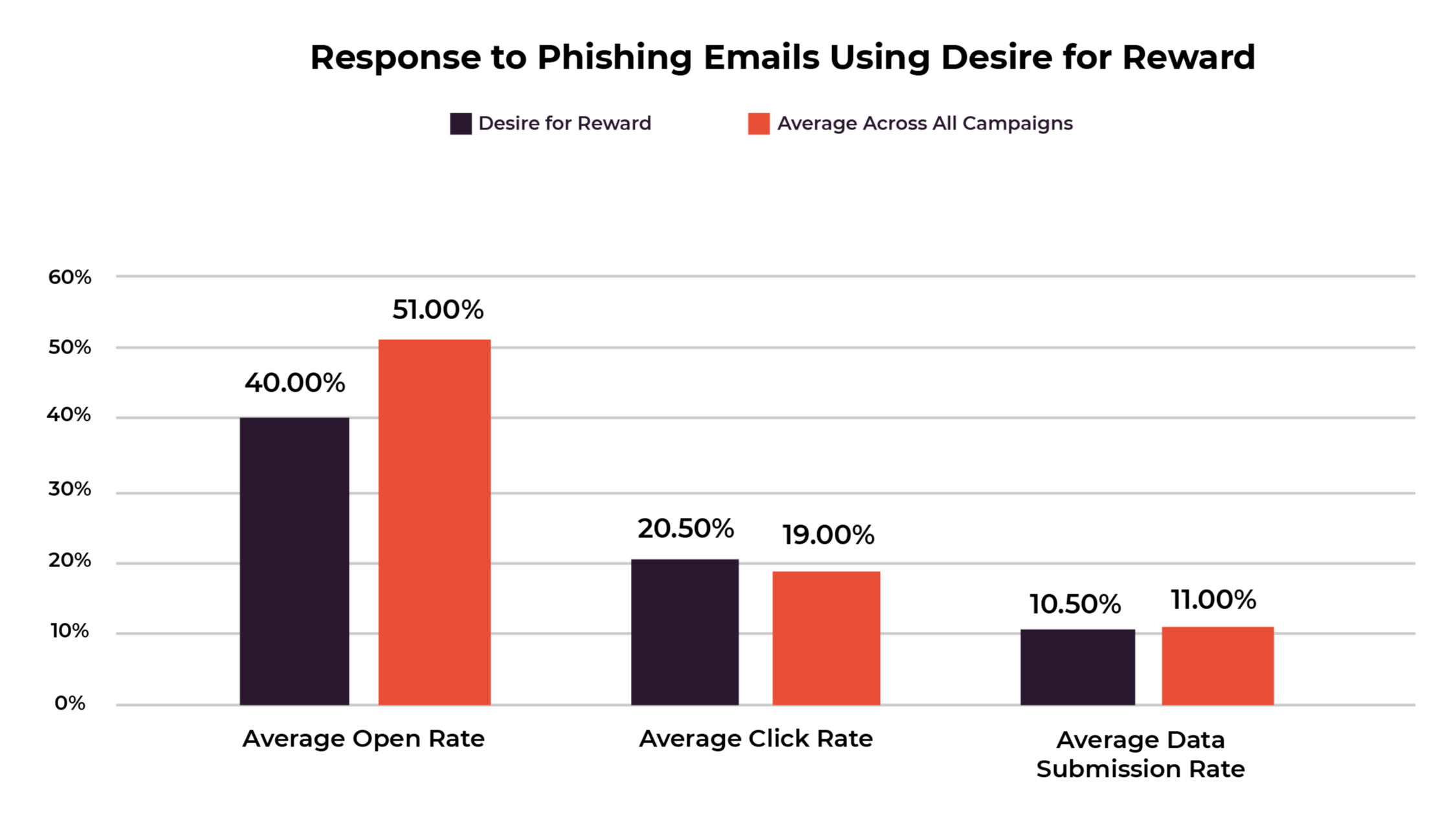
The most successful campaign within this category was a staff competition phishing email. This campaign worked especially well because it combined two potent social engineering techniques: company authority and desire for reward. But our desire for benefits can take over even when the email comes from an external sender. This was the case in the second most successful phishing campaign in this category, which required the recipient to log in to an external website using their company password.
What else can we learn from our phishing campaign data?
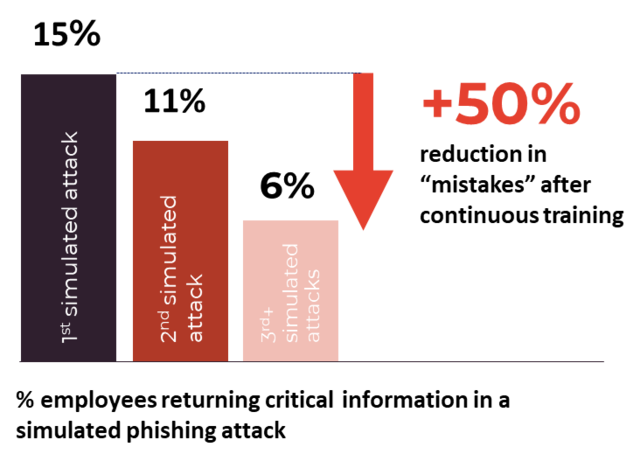
Now that we’ve gone through the top three most convincing social engineering techniques shown in our data, let’s talk about the other trends our data shows. We can see that people tend to have their guard down when an email looks like it is from an internal sender, but it’s important to approach all emails with a healthy amount of scepticism. The differences in open, click, and data submission rates show us that knowing the signs of a phishing email and thinking twice before clicking links prevents phishing email mistakes. Data from another of our studies also show that knowing the signs of a phishing email helps to identify them. Our users made over 50% fewer phishing email mistakes by their third phishing test.
Social engineering technique does not affect people’s actions once they click the link
Across all emails, there is not a big difference in the number of people who thought twice after clicking the link. On average there’s about an 8-10% difference between the number of people who click the link and those who then submit their data. But the difference is about the same regardless of what social engineering technique was used or the topic of the email. It seems that once a person clicks the link, they’ve mostly made up their mind and the email contents don’t matter as much.
This tells us that it’s important to know the signs of a phishing email within the email itself, because once you leave the email and follow the link, the damage could already be done.
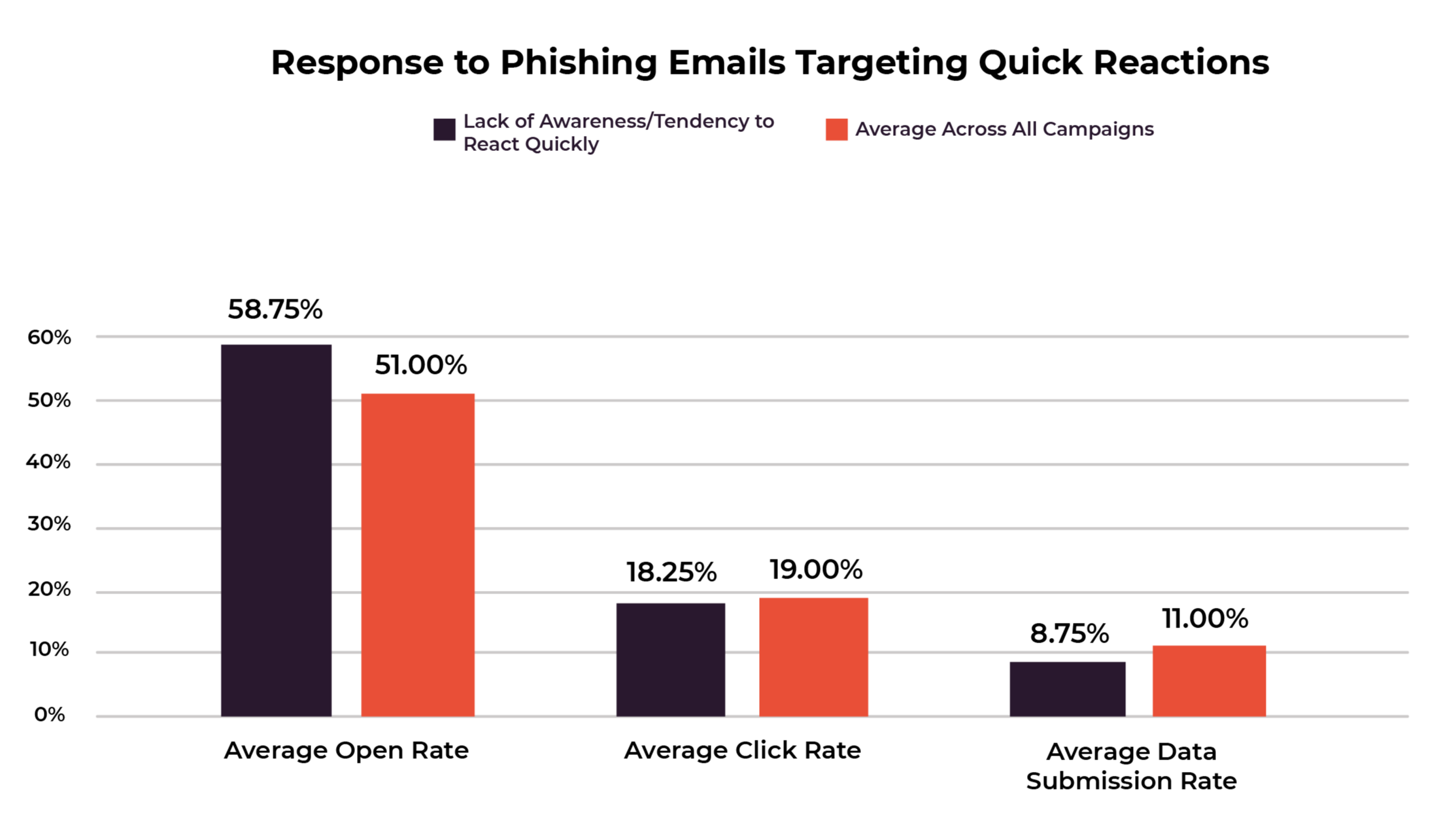
Initial lack of awareness or instinctive reactions can be recovered from
Our phishing campaigns that took advantage of people’s tendency to react without thinking had high open rates but low click and data submission rates. Overall, these emails prompted 59% of people to open them (compared to the average open rate of 51%), but much fewer people actually submitted their data - only 9%. This big difference between the open rate and data submission rate shows that the phishing story isn’t entirely gloomy. Sometimes people open an email without really thinking about it, but then their detective skills come into play. They notice something is off and they avoid falling for the hacker’s tricks.
You’ll see the same trend again in this next section.
Most people are well aware of the threat posed by external email senders
Our phishing campaign where an external company sent employees a survey to take had one of the biggest differences between the number of people who opened the email and those who returned their data. While it had the one of the highest open rates of all emails at 62%, it also had a below average data submission rate (9%).
Openings don’t give us a complete picture of phishing campaign performance, since a lot of people accidentally open an email. The key is the difference between the open rate and data submission rate, as this tells us they saw something in the email that looked phishy, and they changed course.
Overall, this points to the importance of knowing the signs of a phishing email.
Knowing the signs of a phishing email prevents serious mistakes
We can see the same trend in differences between open and data submission rates in other phishing campaigns too. For example, our phishing campaign about a new IT system had the highest open rate of all campaigns. 75% of users opened this email, compared to the average open rate of 51%. But they saw something in the email that told them it was a scam and only 9% submitted their data, lower than the average of 11%.
Phishing characteristics in this email that could have given them the clue were:
- Errors in the sender’s email address or signature
- Hovering over a link shows an unusual URL
- Short deadline
- No prior warning given
As the past few phishing data findings have shown, knowing how to detect a phishing email can encourage people to think twice before doing what the hacker wants.
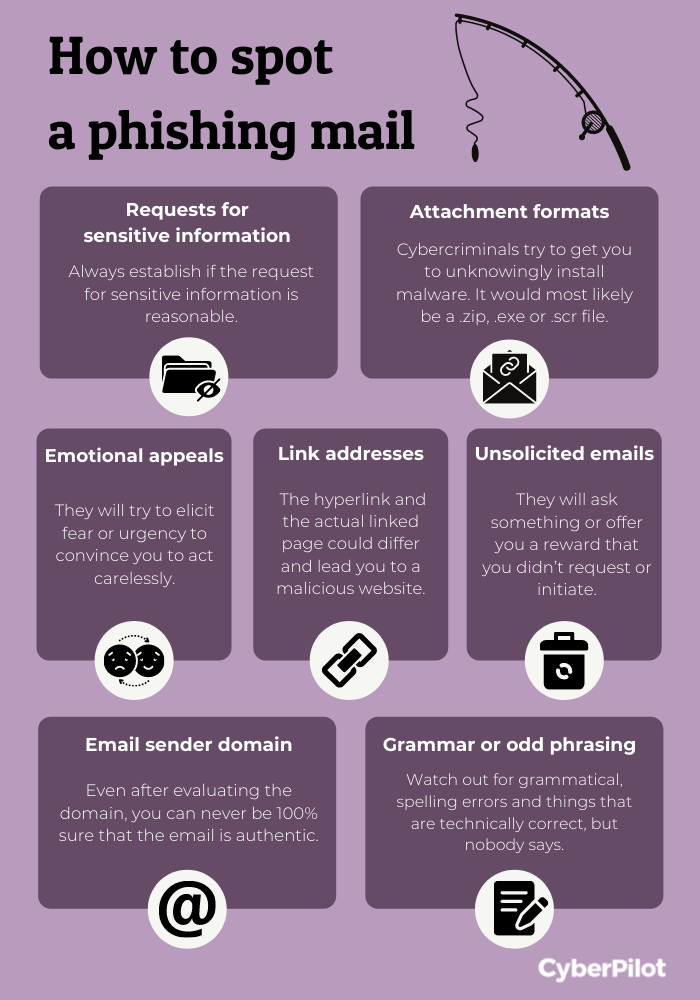
You’re welcome to use our free posters on topics within cybersecurity and GDPR, like the one above on signs of a phishing email.
The messenger matters more than the topic
Another trend in our phishing campaign data shows that it's not necessarily the topic but the messenger that can be most impactful. As we saw, company authority is the easiest weakness for a hacker to exploit. So, even if the topic of an email seems phishy, we’re much more likely to trust it when it comes from a “trusted source.” People are more aware of a benefits scam that comes from a random external sender, but if it comes from their company, they are more likely to trust it. The same trend exists with other phishing email topics, like security updates. Since company authority is so easy to exploit, it’s important for everyone to be aware of hackers who impersonate somebody within your company, as is the case for CEO fraud.
Preventing phishing starts with awareness
The data from our phishing campaigns shows us that it’s important to be aware of the signs of phishing emails, the different types of phishing emails that exist, and the social engineering techniques that hackers exploit. On average, 10% of all phishing email recipients in all of our campaigns submit their data or take the desired action. But it doesn’t have to be this way!
Hackers will always try to exploit human weaknesses. The best way to prevent them from succeeding is being prepared. We recommend training your organization to be aware of different phishing and security threats through security awareness training, and then putting their skills to the test with phishing testing. And research confirms that training works, so it’s worth your time. For instance, our data shows that people make over 60% fewer phishing email mistakes after they have received continuous awareness and phishing training.
The bottom line? Social engineering works, but so does training.


