Keep an Eye Out for These 6 Social Engineering Techniques Targeting Employees
Most data breaches involve a human element, and some form of social engineering is present in almost all cyber-attacks. Cybercriminals use social engineering techniques to gain our trust by exploiting our vulnerabilities. With phishing scams rapidly increasing and becoming more sophisticated all organisations are at risk of being targeted. Knowing about the most common social engineering tactics and the reasons they work can help you recognise these threats, and with the right countermeasures in place, defend against them.
In short
Before we get into the tactics, you should know what social engineering is and how it works.
What are social engineering techniques? Social engineering techniques involve manipulating people into revealing confidential information or performing certain actions. Attackers use psychological tactics to exploit vulnerabilities and take advantage of people's trust and lack of awareness about cyber security.
How does social engineering work? Social engineering makes use of our tendency to trust. Essentially social engineering attacks work because if one thing, scammers understand people, and they are great manipulators that don’t shy from exploiting others.
How can social engineering be protected against? Learning about social engineering can help you understand how criminals use social engineering tactics to get access to systems and data. By knowing about their methods, you stay a step ahead and avoid falling victim to the most common attacks.
Why do cybercriminals use social engineering?
Social engineering is used for many reasons, and we can't list them all here. But, we still want to give you a couple of examples of when cybercriminals take to social engineering:
- To access sensitive data or company secrets that can be used to blackmail the organisation
- To steal personal data about employees or customers to commit fraud, or take out loans
- To obtain log in data to access company networks and systems
- To get people to click on malicious links or download attachments that contain malware
Now that you have an overview of how social engineering works. Let's jump into the more interesting part, the methods!
6 common social engineering techniques with countermeasures to defend against them
Social engineering relies on different methods and may involve multiple steps to accomplish the fraud. Most social engineering attacks happen, at least partly, through social media or phishing e-mails according to Interpool. But it is not uncommon for attackers to approach people in-person or by calling them.
Below you find a list of examples of social engineering attacks and the countermeasures we recommend organisations employ against them.
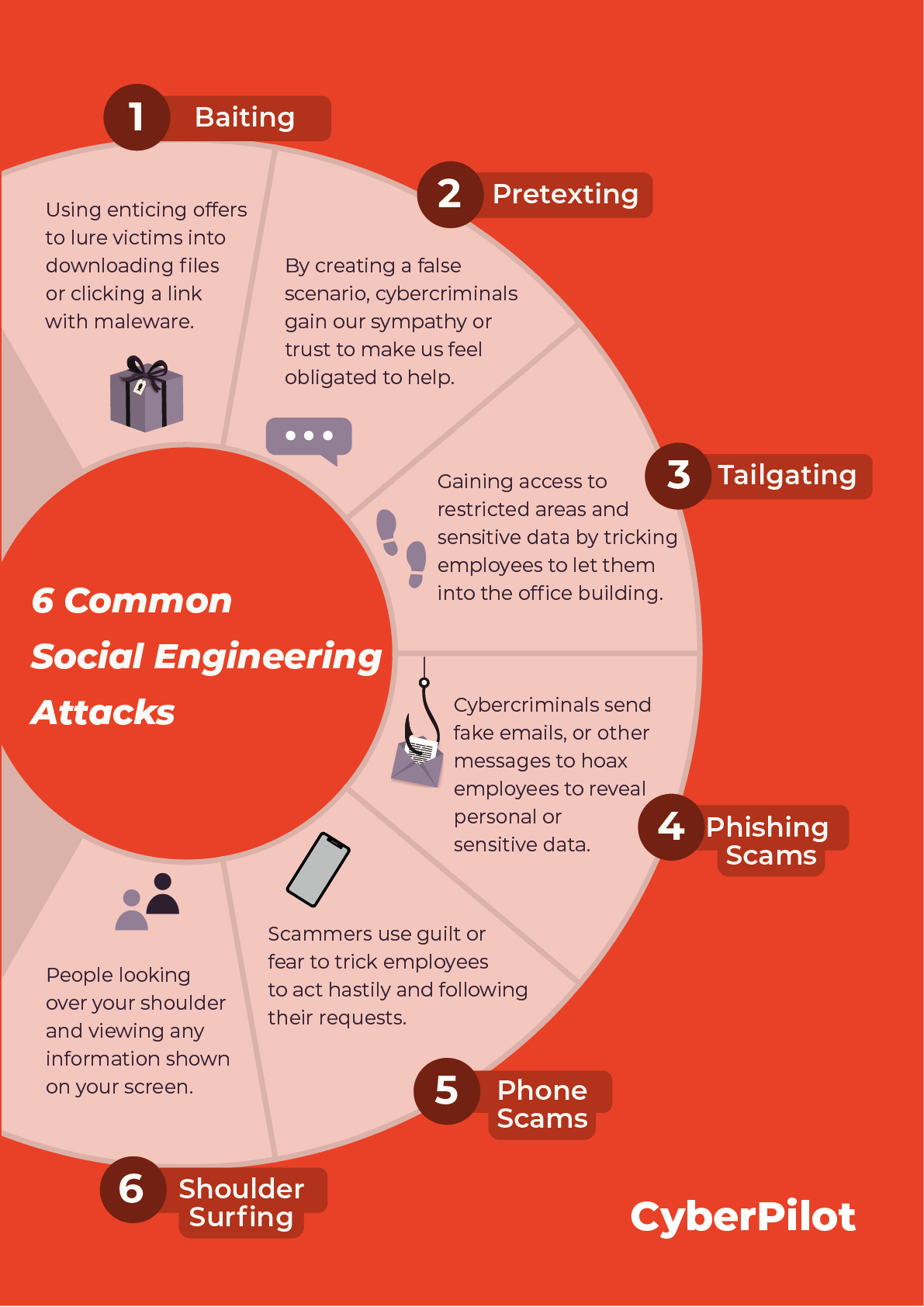
6 common types of social engineering attacks:
- Baiting
- Pretexting
- Tailgating
- Phishing scams
- Phone scams
- Shoulder surfing
1. Baiting – we can't seem to resist free gifts
According to Verizon's 2025 Data Breach Investigations Report, baiting remains one of the least common social engineering tactics, accounting for only 0.5% of incidents.
However, believe it or not, free offers and gifts are still one of the most popular reasons people click on phishing links!
A baiting attack uses enticing offers, such as free software or merchandise, to lure victims into downloading files or clicking on a link with malware.
Why we can’t seem to resist free gifts is partly due to FOMO (fear of missing out) on a great offer which may lead us to act quickly without thinking.
Example of a Baiting social engineering attack
An employee receives an e-mail telling them their employer has partnered up with an external discount website. To receive the discount the employee must log in to the external website using their work-email.
In the example, the employee not only risks clicking on a malicious link, but their log in data could end up in the hands of cybercriminals.
How to prevent a baiting attack
Baiting attacks and phishing e-mails are best avoided by remaining vigilant and aware.
A good rule of thumb is, that if your organisation sends out free gifts or vouchers via e-mail, inform employees about it via an additional channel as well. Tell employees to never accept gifts or vouchers they receive via email, unless it is confirmed via other channels.
Free gifts in e-mails are ALWAYS something that we should think twice about before accepting, especially when it sounds a little too good to be true.
2. Pretexting in cybersecurity – cybercriminals set the scene before striking
A pretexting attack can happen in person, for example, someone showing up at your office guised as a vendor. But, more commonly, pretexting takes place online (like in the example below).
What is pretexting in cyber security?
Pretexting is what makes social engineering scams appear real. By creating a false pretext or scenario, cybercriminals gain our trust or even sympathy, which may lead us feeling obliged to help.
Pretexting appears in 30% of all social engineering incidents, meaning it's one of the most common tactics used by cybercriminals.
Example of a pretexting attack
Mark receives a message on LinkedIn from his colleague Joe. Joe tells Mark, he urgently needs to talk to their manager Ann about a deal their company recently made. The deal is huge, and they even posted about it on LinkedIn earlier this morning. So, Joe sends Ann’s personal number to Mark, not knowing that the person on the other end isn't his colleague Jon, but an imposter.
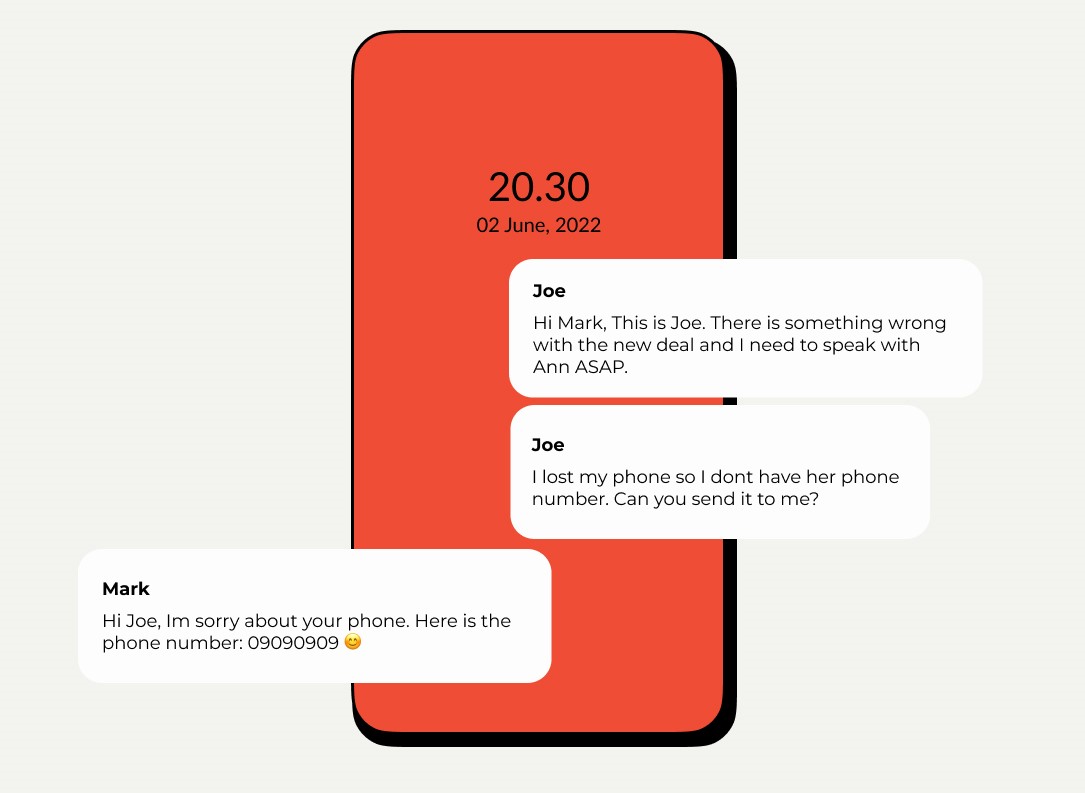
Scammers use social media to pose as people you trust, and their profiles might show mutual friends or list a familiar company as their employer. The scammer uses the pretext to make the scam seem credible, in the example above we can see how creating a false scenario might result in an employee disclosing sensitive information.
How to protect your organisation against pretexting
You can't stop scammers from reaching out to you, but you can prepare your organisation, and your employees, for when they do. Keep your organisation safe from pretexting attacks by informing all employees about the potential risks of scammers reaching out via social media or in person.
If someone you know messages you through a channel, they don’t normally use, or if they ask for sensitive information, it might be a scam. Reach out to the person via another channel or speak to them in person to confirm their identity.
3. Tailgating - a large threat to cyber security
Tailgating, also known as piggybacking, is a social engineering technique used by cybercriminals to gain access to restricted areas.
Examples of how a tailgating attack works
Here are three ways tailgating gets used in cybersecurity:
- The attacker disguises as a deliverer and carries something in their hands that they use as an excuse for not being able to open the door themself.
- Using a pretext, the attacker gives a reason that appear legitimate for why they need to access the area such as a meeting with the company manager about the new salary system.
- The attacker follows an unaware employee into the building, or through a check point by staying close behind him.
Because the thought of a cybercriminal approaching your workplace dressed up as a deliverer or electrician seems so banal, organisations don’t see it for the threat it is. Especially at risk are companies that don’t train their employees and don’t have the right access control systems in place.
Why do cyber-attacks take place physically?
Cybercriminals use psychical methods such as tailgating to gain access to server rooms, restricted networks, or systems to steal customer data, company secrets, or information regarding finances.
How to protect your organisation against a tailgating attack
To protect your organisation against tailgating, you need digital as well as physical security measures. While two-factor authentication can help protect your organisation from unauthorised digital access, social engineering awareness training and limiting physical access with physical barriers such as doors operated by badge readers help you prevent physical threats.
How to train your employees to defend against tailgating
Inform your employees that if they let people into the company, they should ensure they have legitimate business there. If they claim they are there to speak to John, you should lead them to John, ensuring that this is someone John has a meeting with. Don’t let the person roam around the office by himself.
If it is an electrician or deliverer talk to the person in your organisation that ordered the service before you let them in to ensure they have reason to be there.
4. Phishing scams
The Verizon report also highlights that phishing remains the most common social engineering method, accounting for 57% of all incidents.
Phishing, vishing, and smishing are methods that rely on emails, phone calls and text messages to send out fake messages.
Spear phishing or targeted phishing is an attack tailored to trick a specific person, such as an CEO, but it can also be an unaware employee. To tailor the scam message, the attacker will research the company's website and social media channels, to find out who works there, where it’s located, upcoming events etc.
Example of how a phishing scam could be carried out
An employee receives an e-mail from what appears to be the HR-manager, inviting the employee to the upcoming company party and asking them to register through a link. The employee has long been excited about the party and was waiting to receive the invitation. The employee is not suspicious towards the email and fails to identify it as a phishing email, clicking the registration link. 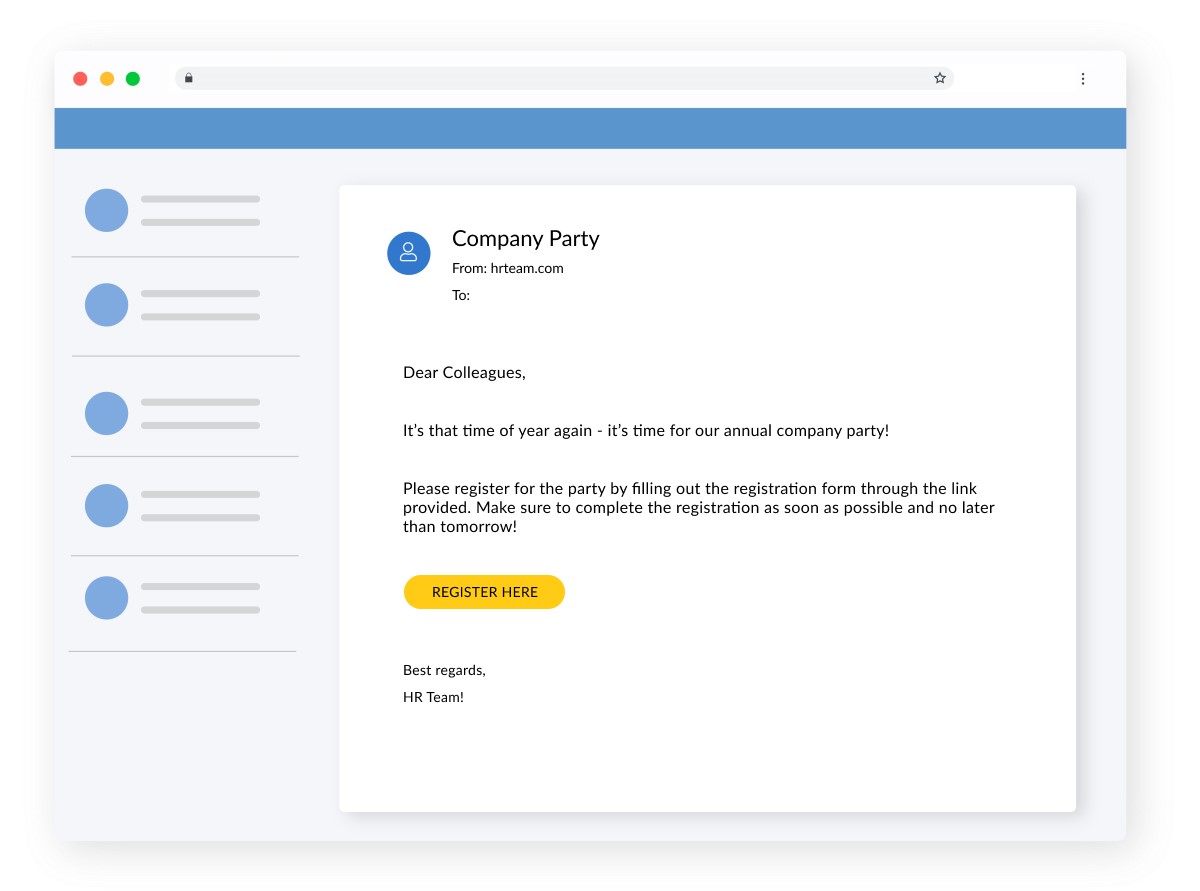
The most common social engineering methods according to the over 100,000 phishing emails we sent out
Cyberattacks constantly evolve to avoid detection, and while some methods stay the same, others develop into new ones. To learn what social engineering techniques work the best we looked at the over 100,000 phishing emails we’ve sent out over the years.
Turns out authority, urgency and reward are the social engineering tactics with the largest success rate and what gets most people to click on links in phishing e-mails.
Phish your colleagues to avoid phishing scams
Phishing simulations or phishing training is a method used to test your colleague's ability to recognise and respond to phishing e-mails. When done correctly, phishing your colleagues can significantly improve your organisation’s defence against phishing and (social engineering attacks).
If you decide to do your phishing training with us, you'll love the advantage of planning your phishing campaigns with our experts right in the app. This way, you get a collaborative approach that ensures a solid strategy to protect your organization against cyber threats.
Learn more about the benefits of phishing testing
5. Phone scams
Phone calls are an effective social engineering technique because, by speaking directly with the victims, the attacker can more easily manipulate them. By exploiting feelings such as guilt and fear we are more inclined to act quickly and may follow the requests of someone calling us demanding urgency.
We tend to be a lot less considerate of cybersecurity when using our phones than computers. But phone scamming is the most common form of phishing attacks after e-mails. It is therefore important that employees have awareness of how to use their phones safely.
Example of a phone scam
An employee receives a phone call from a person claiming to be the company's external IT-support. The employee is unaware of this service, but he has noticed his computer working slower lately. The caller confirms that this is the problem and asks the employee to download a repair program sent to his e-mail. Scared of causing further damage the employee downloads the malicious program.
How to protect your organisation against phone scams
Phone scams are diverse and can be difficult to prevent. These steps will help you avoid the most obvious threats.
- Never give out sensitive information over the phone e.g., credit card information. Ask the caller to follow up on email and look up the company website yourself to see if it's legit.
- Make employees take a course, teaching them how to avoid phone scams
- A MDM system can help you monitor how employees use their phones, making it easier for management to keep track of potential phone scams.
Only one more method to go before reaching the end of our list of tactics.
6. Shoulder surfing and working on the go
Many organisations allow employees to work from outside the office, at home or on the go, in cafes, hotels, or trains. This is a mayor convenience, that many of us enjoy. But it also poses additional security risks!
Working in crowded places can result in shoulder surfing. Shoulder surfing is when another person looks over your shoulder to view information on your screen such as log in details, or confidential information.
Example of how shoulder surfing can happen
An employee, working in a café receives a phone call. Other people in the café might be curious and listen in on the call, or they might use the call as an opportunity to view information on the employee's laptop screen.
How to stay safe when working remote
When working on the go it's important to be aware of our surroundings and pay attention to ensure no one can view our screen or overhear phone conversations.
Be sure to always lock your screen when away from your device. Another countermeasure to consider is tinted screen protectors that limit shoulder surfing.
So, these were some of the most common methods. Although, very different they all have one thing in common - lets take a look at that next.
Social engineering techniques work by exploiting human emotions
All social engineering methods rely on exploiting human emotions and trust. This is not a technique in itself but it's a major component of what makes social engineering attacks successful. Attackers can manipulate our willingness to be cooperative colleagues and to help those in need, as well as our fear of failure by triggering emotions such as kindness, desire, fear, or guilt.
When it comes to cybersecurity any request that evokes a strong emotional response should be met with caution!
AI tools and Deepfakes increases the success rate of social engineering attacks
Advancements in technology has made it easier for hackers to create cunning types of social engineering attacks, that appear legitimate. With AI tools such as deep fakes and ChatGPT rapidly increasing in popularity among cybercriminals, its important to know about these threats.
What is Deepfake phishing?Deepfakes allow cybercriminals to generate text, audio, and video that mimic real, trusted people Deepfake phishing has been around since 2019, when a UK-based company transferred 220,000 euros, after an employee received a phone call from a cybercriminal using deepfakes to mimic the company CEO. Deepfakes are now used in various scams such as fake job applications.
Learning about the use of AI technology in phishing is an important step in mitigating the risks. To prevent faulty financial transactions or handing out confidential information to the wrong person its especially important that top managers and those in decision making positions are aware of AI scams.
What is the best countermeasure against social engineering?
While there is no one-size-fits-all solution to stop social engineering attacks, combining several countermeasures can help you mitigate the risks.
Popular countermeasures against social engineering
The most effective strategy is to educate your employees on security risks and how to defend against them. Security awareness training is always worth the cost with a ROI of up to 562%.
Data from one of our studies show that knowing the signs of phishing makes it easier to identify scam e-mails. After receiving our training users made over 50 % fewer phishing email mistakes by their third test.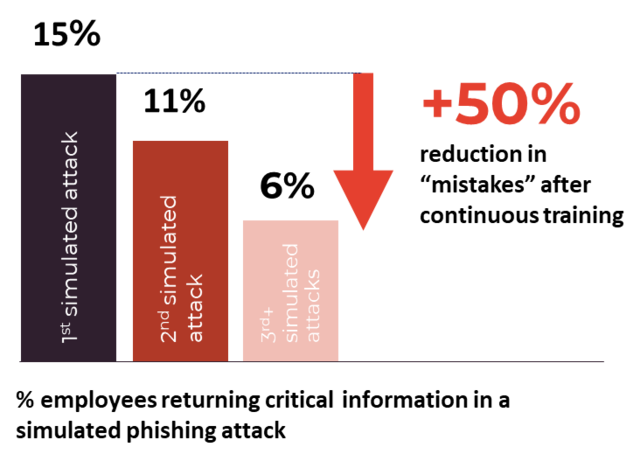
Time matters, the sooner an attack gets reported, the less severe and costly the damage will be. Train your employees to recognize suspicious activities and report them in time.
The right tools and systems can help keep programs and data protected. I.e., in the case of a security breach, multi-factor authentication, can be what saves you.
Prepare employees with phishing simulations. There is no better way to learn how to spot phishing attacks than being exposed to them on a regular basis. Phishing simulations work because they are as close to reality as it gets.Only focusing on IT is not enough to keep your organisation protected. You need to consider the human side too!
What should you do when you are the victim of social engineering or phishing?
Although, we hope this won't become the case for you here's a short overview to limit immediate harm.
If you find yourself victim to a social engineering scam, the exact steps you should take will vary based on the situation and type of scam. But you can use the following countermeasures in most cases:
- Disconnect yourself from the internet as quickly as possible. Without internet connection, it is harder for attacker to access your device, and spreading viruses to other devices and systems.
- Change your password. If an attacker has gained access to your log in detail, change your password as quickly as possible to prevent the attacker from gaining access to your account. If you are reusing the password for other accounts, change those too.
- Reach out to the person responsible for IT. Your It team can run anti-virus scams and detect impact from the scam. They will know what to do and how to manage the attack from here.
At CyberPilot we believe in taking a proactive approach to cybersecurity. This means you take measures before an attack happens. To prepare yourself for cybersecurity risks and threats we recommend you have a emergency response plan for how you will act in the event of a cybersecurity incident.
Increase awareness with phishing and social engineering training
It’s estimated that in 2022, a data breach happened every 11 seconds, with the average breach costing $4.35M. Most data breaches could be prevented if employees were more aware of how to identify and report phishing and social engineering attacks correctly, which can be achieved with training.
What is social engineering training?
Through social engineering awareness training, employees learn how to spot and avoid phishing scams and other exploitative tactics used by attackers.
With the right training, individuals and organizations can take proactive measures to protect digital and financial assets and keep sensitive data protected.
Don’t wait for a threat to happen instead take proactive measures to mitigate the risks.
Phishing simulations and awareness training helps you take control of the situation by making your employees less of a security risk. Other proactive countermeasures include performing a risk analysis or implementing an IT security policy.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.