Risk Analysis Template and Step-by-Step Guide (Free Example)
Short Summary
- A risk analysis is a process of identifying and analyzing potential events that may negatively affect individuals, assets, or an organization, and planning how to mitigate those risks.
- It helps you prioritize your security activities and determine your tolerance for different risks.
- We take you through our step-by-step guide on how to create a risk analysis using our free template with examples of different risks an organization might face.
Please note that our risk analysis template and guidance focuses on assessing business risks. If you are doing a GDPR risk assessment, you should see the risk from the point of view of the data subject. The EU has a template and guide you can use to do a Data Protection Impact Assessment for GDPR.
Table of contents
- What is a risk analysis?
- Risk analysis for information security
- How to create a risk analysis
- Your security risk assessment is complete!
What is a risk analysis?
A risk analysis is a useful tool for any organisation that wants to anticipate incidents and plan how to mitigate potential risks. It involves identifying and analysing potential events that may negatively affect individuals, assets, or the organisation. A risk analysis can help us make judgements about our tolerance for certain risks so that we can better anticipate them. And most importantly, it makes it possible for us to prioritise our security activities.
"The beauty of risk analysis lies in its ability to unveil vulnerabilities, enabling proactive measures that significantly ease the daily work burden. It transforms uncertainty into a manageable landscape, providing clarity on where attention and resources are most needed." Nathan Clark, Co-Founder of gate2ai.
At CyberPilot, we use this IT risk assessment template to help organisations do a risk analysis for information security.
A cyber security risk assessment can benefit your organisation with the following:
-
Identify vulnerabilities
-
Provides a good overview
-
Determine better processes and requirements, which improves planning
-
Document due diligence
It can also help you understand the probability of theoretical risks happening in real life.
That way, you can better understand how to allocate resources to prevent them. We will give you two examples below.
Listen to our podcast where we go through the risk analysis
A tornado hits your company headquarters and damages all the IT equipment.
While this is certainly a risk that could happen and have a big negative impact, it is unlikely to happen if your area has no history of experiencing tornados. Therefore, your efforts could be better spent thinking of solutions for other risks.
Consequence: HIGH
Likelihood: LOW
A staff member travels with company IT equipment and it gets damaged on the baggage carousel.
While losing the IT equipment of one staff member is not catastrophic for the company, it is more likely to happen if staff travel regularly. And maybe the consequence for losing the specific equipment is not only the cost of the laptop, smartphone, etc., but could also lead to potential data loss or could be one of the breaches against the GDPR that result in a fine.
Consequence: MEDIUM
Likelihood: MEDIUM
We would suggest spending some time on mitigating this risk.
Ultimately, a security risk assessment can help you weather any storm, or at least be better prepared for it.
For an information security risk assessment, we can start by looking at potential events that can negatively affect your organisation.
Some examples include:
-
The website crashing
-
IT equipment being damaged
-
GDPR violation and fines
-
Loss of intellectual property
You can ask yourself:
-
What do those events mean for my company?
-
What resources and assets would I lose in the event?
-
What resources and assets would I lose when trying to fix the problems?
-
What would we do if any of those events happened right now?
In the next session, we will discuss how to create your own risk analysis, using our free risk analysis template as an example.
You can download our template and follow along.
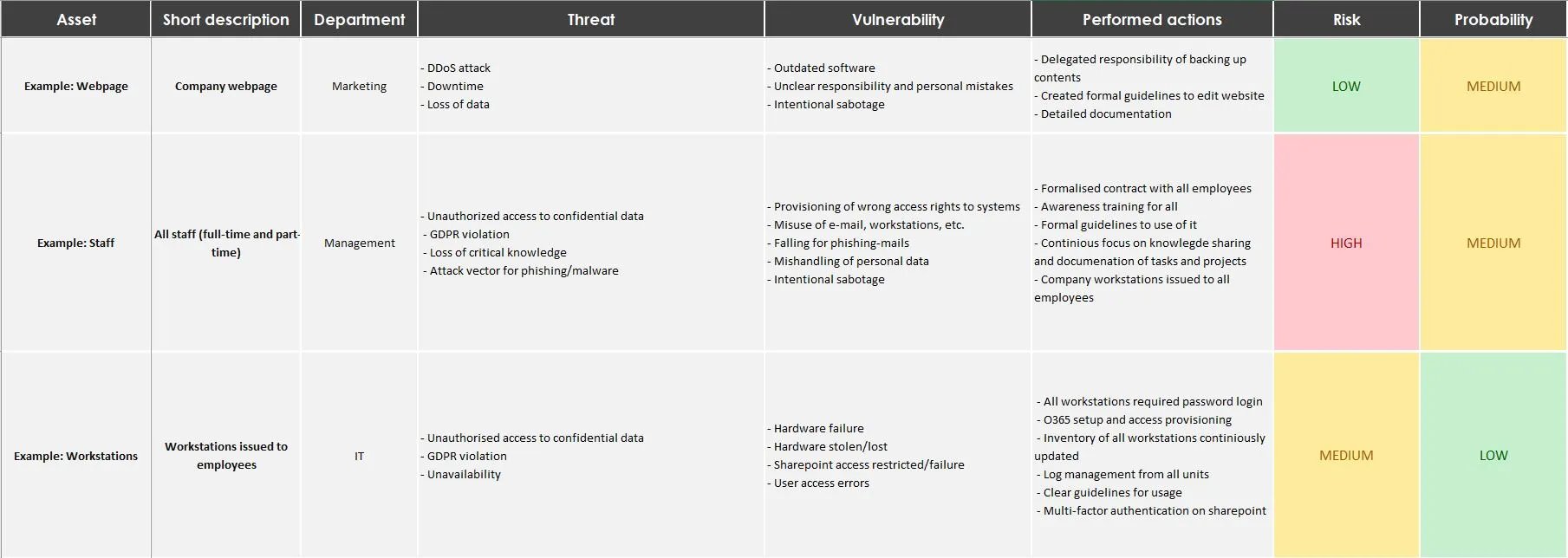
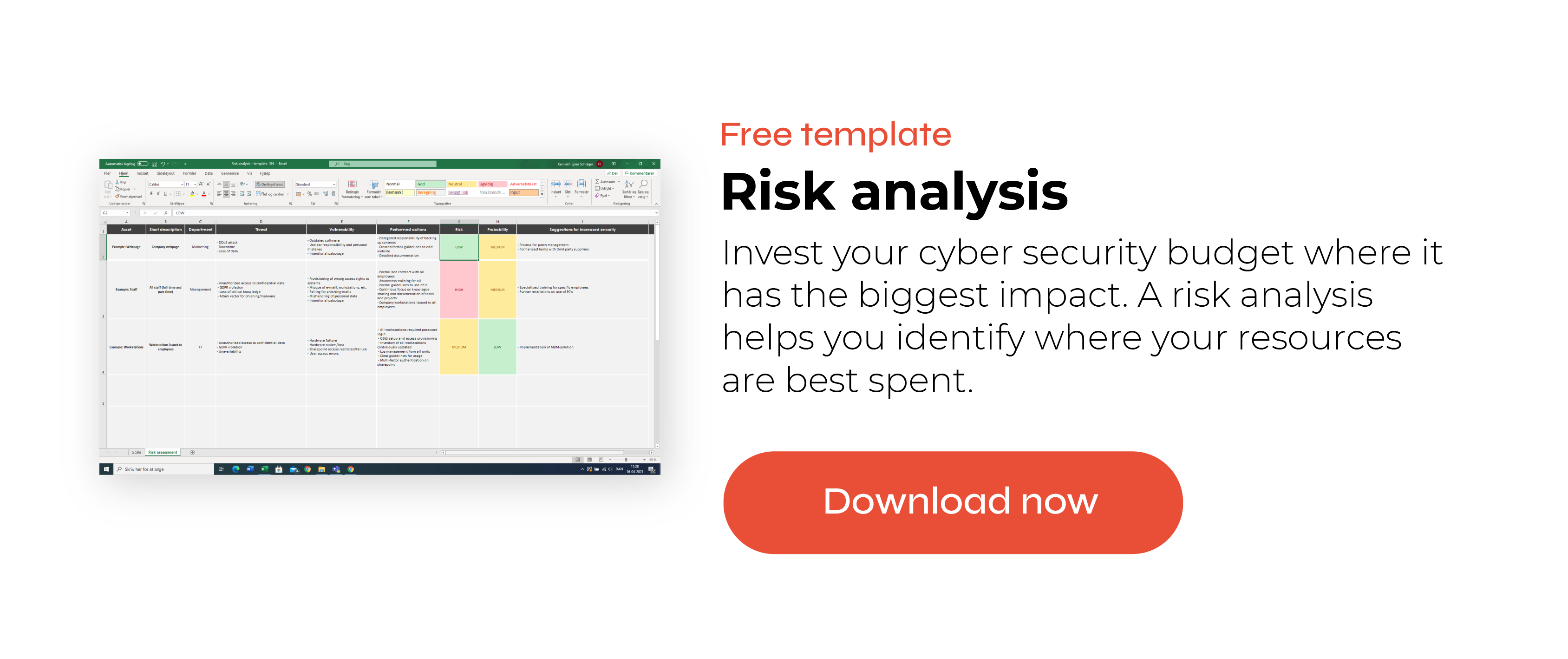
A snippet from our risk analysis template
First, we determine the scales that we use for our security risk assessment. In our template, you can access the scale in the first tab.
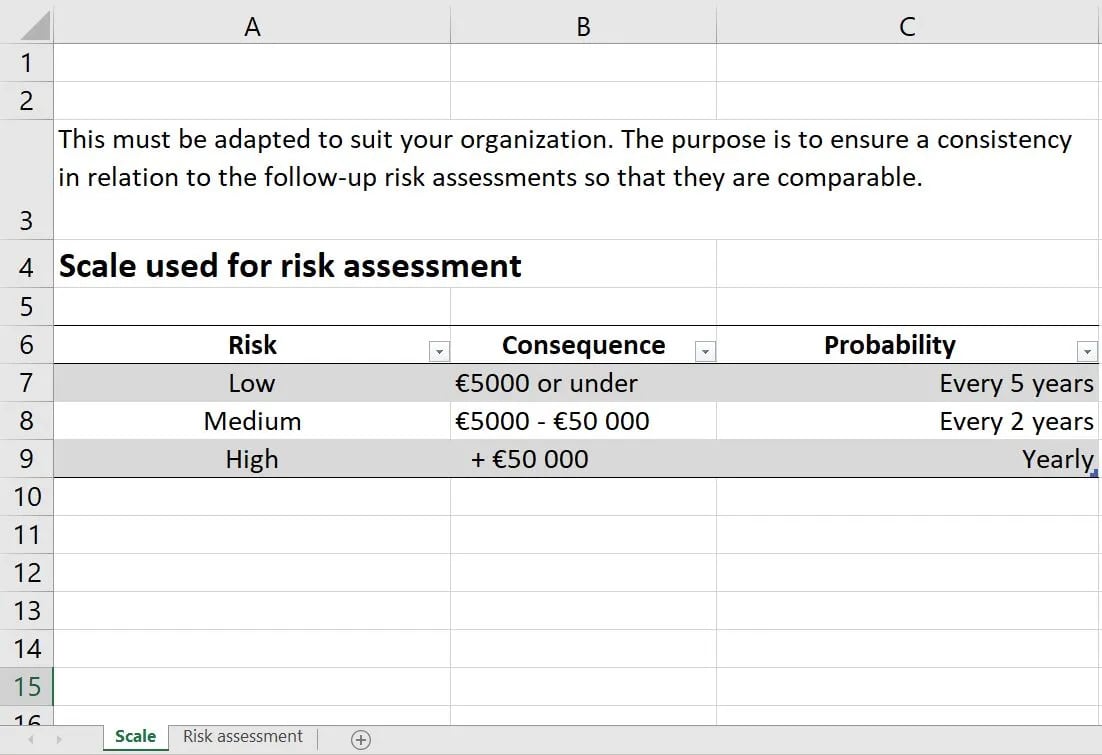
In the risk analysis template, we categorise the risk levels as low, medium, or high. One way of thinking of risk level is how severe the consequences can be for your organisation. Below, we define what each risk level could mean in terms of IT systems.
Low risk
-
The system is easily recoverable
-
The system provides a non-critical service
Medium risk
-
The system provides a normal service
High risk
-
The system provides a critical service for the entire organisation
You can also take this opportunity to discuss within your organisation how many resources you would have to use to fix these issues if they were to occur. Our IT risk assessment template gives you the opportunity to fill in the time and monetary consequences, so you can consider the full impact of different IT security risks.
As the risks and consequences differ from organisation to organisation with smaller companies also in need of cybersecurity, we highly recommend adopting this section according to your needs. For example, if you are part of a company whose revenue comes solely from the online shop on the website, then the website crashing is considered a much higher risk. In contrast, if your website serves just as a landing page without much functionality or effect on your day-to-day operations, then the website crashing is a lower risk because the consequences are lower.
Fill in the security risk assessment
To complete the risk analysis, our template has different columns to fill in:
-
Asset
-
Short description
-
Department
-
Threat
-
Vulnerability
-
Performed actions
-
Consequence
-
Probability
-
Suggestions for increased security
Below, we’ll describe each of these categories with examples.
Asset
When we talk about assets in this context, we mostly mean assets related to your organisation’s IT. This can include hardware, such as laptops and mobile devices that your staff use. You might want to consider implementing a device management system, if you do not already have one in place, in order to keep track of your organisations mobile devices.
Additionally, assets can include the IT services provided by your organisation, such as internal communication systems (e.g., Microsoft Teams of Slack) or customer-facing services like the company webpage. Other than IT assets, we include staff as an asset, as employees have a lot of influence over the state of your information security and can be the biggest defence when it comes to IT-security, which is why it is important that they are aware of the security risks and have received awareness training for complying with the GDPR. We discuss this further in our free e-book on IT security defence if you want to read more.
Finally, if you use IT asset management, then it is very easy to use that document as a reference. You don’t have to list all of your company’s assets, but you can choose the most important or commonly used ones to start with.
Short description
Although self-explanatory, this column can be very useful for defining what you mean when you list different assets. For example, when we list staff as an asset, we can define it as both full-time and part-time employees. You can also define who is not included, for example, consultants, who act as external advisors to the organisation but are not officially part of the organisation.
Department
Defining which department is responsible for each asset is advantageous because it prepares the company to respond when an issue must be fixed. Maybe instead of an entire department, it’s the Data Protection Officer who is responsible. Laying out responsibility is useful for a few reasons.
First, it can give you a better understanding or a refresher of each department or sub department's responsibilities. Second, clearly defined responsibilities can help the organisation react faster when there is a security risk.
However, we don’t recommend spending too much time on this column, as responsibilities can easily overlap between departments and change over time. We recommend getting a general understanding and being flexible when it’s time to fix the issue.
Step 3 - List threats and vulnerabilities
Threat
A threat describes any potential damage to an asset, which could affect the organisation. If there have been any security breaches or incidents in the past, you can list them in this column. For example, ransomware and malware or unauthorised access to confidential data could be considered threats.
For instance, the threat of ransomware often occurs through websites, for this reason you should make sure all staff members knows how to brows safely while at work. They may unsuspectedly stumble upon a fake website and accidentally install ransomware, therefore locking access to the organisation’s files and their computer until they pay the cybercriminals. Next, we discuss vulnerabilities that coincide with these threats.
Vulnerability
Vulnerabilities can be described as the reasons for why threats occur. When it comes to ransomware, vulnerability might occur from staff members unsuspectedly stumbling upon a fake website and accidentally installing ransomware.
While vulnerabilities can also occur through unauthorised access to confidential data. In this case the vulnerability could be somebody forgetting to close the browsing window after a video call, and accidentally showing a customer their internal communications. Knowing how to prevent data breaches through video calls is therefore an easy step to decrease vulnerability. One of the most common security breaches happen due to people sending emails containing personal data to the wrong person.
The purpose of this section is not to place blame, but rather to think of potential security risks and the reasons why they might occur.a) Understand how big the threat is
b) Predict the probability of the threat happening
c) Think of ways to proactively avoid threats
Performed actions
In this section, you write whether you have already done anything to mitigate these risks. For example, if you have experienced losing important files before and now use cloud storage for back-up, that is an example of a performed action. If you use awareness training or phishing simulations to keep IT security top of mind for your employees, you could also list these activities here.
Consequence
After writing about the threats, you can better assess how big the consequences would be if they were to occur. This is obviously a subjective assessment, but it should be discussed with colleagues. Often, you will find that your colleagues have different perspectives on the consequences. Perhaps the marketing department will put a ‘HIGH’ consequence on something happening to the company website, since that can affect sales. But the IT department would not see it in the same way, as it would not affect the day-to-day operation of the company. That’s why it is important to get a lot of different perspectives when you evaluate the consequences.
Probability
Not all risks are created equal. Some could probably happen a few times a month, while some may only happen once every few years. By assessing the probability of threats, you can understand how to prioritise them, and perhaps leave out the ones that you can’t realistically tackle.
Suggestions for increased security
After filling in the previous sections, you will have gained a better understanding of each asset and the risks associated with them. In this section, you can use your answers from the previous sections to write down suggestions for increased security.
When every section is filled in with the assets and the threats you can think of, you will have a better overview of the risks to your IT security. From the risk analysis, you will be able to see which threats are more likely to happen and the consequences if they occur. Of course, you can keep this document handy and update it regularly. It can even be a document you consistently refer to, like your IT Security Policy and Acceptable Use Policy.
We hope that this blog has helped you understand what a security risk assessment is and how to do one yourself. As a matter of fact, we use this risk analysis template to help many organisations who want to have a better understanding of the security risks to their IT assets. If you would like to get some help with putting together your risk analysis, we are happy to have a talk about it. Download our template here and you can contact us at info@cyberpilot.io.
People also asked
What is a risk analysis?
Risk analysis is a procedure that involves identifying, assessing, and evaluating potential risks and their impact on an organisation, project, or system. It entails examining the probability of a risk occurring, its consequences, and devising strategies to prevent or mitigate those risks.
What does a risk assessment include?
A risk assessment typically includes identifying potential hazards, evaluating the likelihood and potential impact of those hazards, determining existing controls, and making recommendations to reduce or eliminate risks. It may also include prioritizing risks, setting risk management goals, and creating an action plan to implement those goals.
What are the steps of risk analysis?
The steps of risk analysis include identifying and assessing potential risks, evaluating the likelihood and impact of those risks, determining risk tolerance and prioritisation, developing risk mitigation strategies, implementing controls and monitoring effectiveness, and periodically reviewing and updating the risk management plan.
You can also watch our video about how to fill out a risk analysis right here
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.