How To Do Good Phishing Simulations
Phishing is one of the most common methods of attack for cyber-criminals. That’s why training your employees to recognize and respond to phishing emails is a key part of many IT security practices. In this blog post, we give you a guide on how to implement phishing testing within your organisation and some free sample phishing campaigns that can inspire your own work.
Why phishing tests are important
Phishing is one of the most dangerous IT security risks for any company and it’s also one of the most common kinds of attacks companies experience. On top of that, data breaches caused by phishing attacks are extremely expensive for companies to respond to. This year, breaches resulting from phishing attacks cost a company $4.65 million on average. That’s a lot of money to lose from what seems like a tiny email mistake!
Since phishing poses such a big threat to organisations, it is important that employees can recognize these emails when they receive them, so they don’t fall for them and reveal sensitive information. Teaching employees to recognize and respond to dangerous emails through phishing testing is a great way to let your staff practice in a low-stakes environment. Results from the tests can also help you understand if there are any gaps in your IT security training that need to be filled.
Guide: How to implement phishing testing
If you are going to begin a phishing training programme within your organisation, you should spend some time getting organised at the beginning. This will save you time once you launch the programme and help everything run smoothly. Keep reading to see our suggestions for starting a training programme of your own!
Getting the phishing testing programme ready
Decide if you want to let your office know
Before you send out any phishing simulation emails to your staff, you should decide how much you want your staff to know about the new training programme. Depending on your staff, you may decide not to communicate about the programme, so that you can get a completely realistic result to the test emails. However, if you know your office may feel sensitive to being tested without their awareness, it could be best to let them know about the phishing simulation ahead of time.
If you decide to keep the programme a secret at first, you could benefit from more realistic phishing test results initially. Since your staff aren’t expecting a phishing email, you can get a more realistic sense of their awareness and vulnerability to real attacks. However, keeping the programme hidden from employees risks your staff potentially feeling judged or misled - especially is you use the test results to single out specific individuals.
On the other hand, communicating about the programme before you send the first phishing test email can foster efforts to maintain open communication within your office. It can also serve as a convenient time to remind everyone in your office about safe IT security practices, such as what fishing is, how to recognize it in their inboxes, and what could happen if they send sensitive data inappropriately.
Choosing whether you want to let your office know about the programme can be difficult, but if you take your office culture and your staff’s best interests into consideration, you can make a decision that is right for your team.
We’ve found that our customers usually prefer not to inform their userbase before the first test, but communicate about the phishing testing programme after the first test. This mixed approach could be a good fit for your staff too.
Remind staff of your reporting process
If you tell your staff about the phishing testing programme ahead of time, it is also a perfect time to refresh everyone on the reporting and response procedures in place. Make sure everyone knows what they should do if they suspect a malicious email in their inbox: Who do they report it to and how? What should they do and NOT do with the email?
If you choose to keep the programme hidden at first, the initial phishing test email can give you important insights into how well your team understands your reporting procedure. Sometimes, employees think there are 3 or 4 different places where they should report suspicious emails. In our experience, determining how well your staff understands how to report IT threats is one of the primary insights our customers get from phishing test campaigns. After the first phishing test has concluded you can convene a meeting to discuss the programme with your staff and provide a quick refresher on best practices.
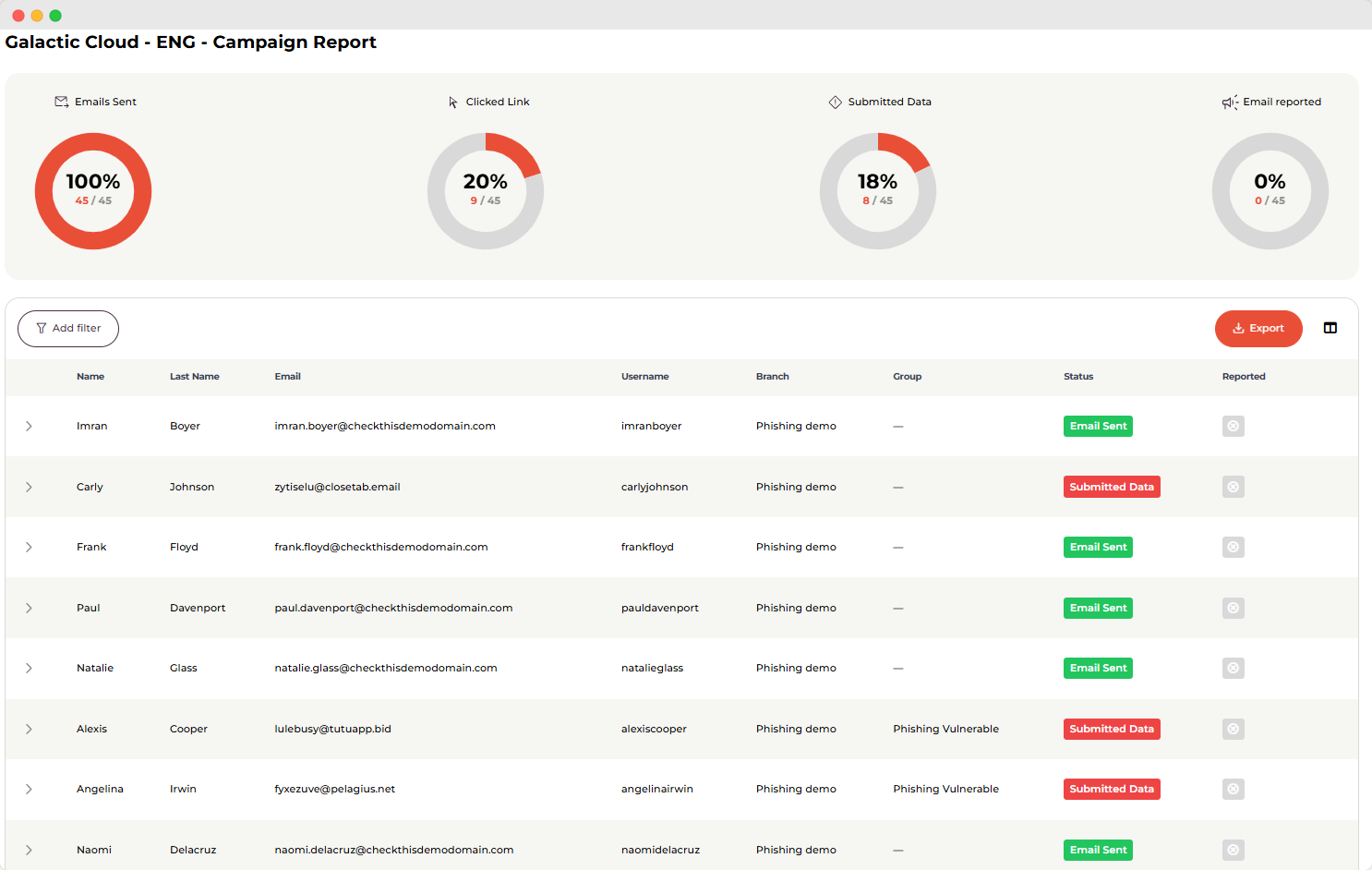
(This is an example from our own platform of how it looks when results are coming in from a simulated phishing training)
Tips for writing a fake phishing email
If you are not cooperating with a phishing training provider, you will probably spend some time creating the phishing emails that will be sent to your employees. To train your staff to recognize these emails in real scenarios, it’s important that you make the emails believable and use the same methods that cyber criminals use. Before you get too worried about crafting the perfect test emails, below are a few tips you can use to get started. You could also ask ChatGPT to help you, but we won't cover that in this post.
 (Here's an example of one our own simulated phishing mails)
(Here's an example of one our own simulated phishing mails)
Use common phishing signals
Although phishing emails often look different, there are a few common characteristics that some phishing emails have. For example:
-
Use of bad grammar or misspelled words
-
General or unusual greetings that are not commonly used
-
A sender domain or email address that looks off
-
Attachments that have an unfamiliar extension
-
Links that look odd or are unrelated to the linked text
-
Urgent requests for sensitive data (e.g., login credentials or credit card information)
These are a few basic phishing-signals that you can include in your emails, and they are a good starting point to keep in mind when you write your test emails. If your team has a good understanding of phishing, these tells might be too easy for them. For example, the use of bad grammar or spelling mistakes is becoming less and less apparent in phishing emails, as the cybercriminals get better and our spam filters catch more obvious phishing threats. To make the training more effective, you can mix in other signals that make the emails more difficult to detect.
Make the emails enticing
For a phishing attack to be successful, the recipient must feel the need to act. Pair some of these tactics below with the basic phishing signals to make your training emails even more effective:
-
Request an urgent or time-limited action
-
Make it emotional (fear and excitement work well)
-
Offer a desirable reward
-
Use authority figures to exploit their sense of trust (see our post on CEO Fraud)
Adding these techniques will make it more difficult for your employees to resist clicking an email.
Remember: the more real your emails look, the stronger your team will become at detecting malicious emails.
You should also keep up to date with current trends in phishing emails so you can include them in your tests.
Here are four examples of phishing campaigns that we have created and tested on our customers.
Establish a schedule
You will also want to decide how often you plan to send phishing test emails to your organisation so you can create a continuous training schedule. Of course, this schedule can be adjusted throughout the training process as you go. Depending on your goals, you can even send phishing tests more frequently to staff who failed previous tests.
If you choose to do your phishing training with us, one major advantage is the ability to plan your phishing campaigns alongside our experts directly within the app. Also our platform makes it easier for you to plan and schedule your phishing campaigns months in advance.
But how often is enough?
We recommend sending phishing test emails at least twice per year, but four to six times each year would also be good if you have the resources. The main thing to consider when choosing how often to run simulations is that you want the testing to be frequent enough to maintain continuous awareness without your employees becoming “numb” or burnt-out. Raising awareness is crucial, but too much testing runs the risk of your staff waiting around for the next phishing test instead of exercising their detection skills.

Sending the phishing test emails
Once you have communicated about the training, drafted a few emails, and created a schedule, you’re ready to start sending the emails!
The first test email you send should be mid-level. This allows you to get a realistic understanding of how your staff would respond in the case of a real phishing email. Depending on your goals for the phishing testing programme, you could also start out with a difficult email. This can be useful if you want to show your staff how dangerous phishing emails can really be. The results from this first test will serve as a benchmark that you can use to measure your staff’s progress as they learn.
Prevent the test from getting too easy
Over time as your staff get better at recognizing the phishing emails, you can make the tests more difficult. One way to do this is to make the email look like it is coming from an internal sender instead of an external sender. We usually have our guards down when we think an email is from a colleague, which makes “internal” emails more believable. This kind of test is important because finding the names and roles of people in your organisation is usually an easy task for cyber-criminals, especially if your company has an “About Us” webpage or if your staff use LinkedIn. We view a request for banking information differently when it comes from our finance department instead of a “Nigerian prince!” Switching up the sender makes the email more targeted and will teach your staff to recognize a dangerous type of phishing called spear phishing.
Another strategy you can use is sending emails to only a few employees at one time. This will help avoid the problem of word getting around so your employees can test their skills on their own. We also recommend running different themes for your phishing simulations, because a theme could be easy for some and not for others.
Phishing testing programmes are like going to the gym
After the phishing simulation programme has been in place for a while, it can be tempting to let it slip from your to-do list. But it is important that you keep the programme going, even if your employees continuously return high scores on the tests.
In this way, phishing testing is a lot like physical fitness! If you lift weights every day for half a year, you will probably feel strong and you might think you don’t need to exercise any more. But if you suddenly stop going to the gym, your muscles will grow weaker, and you’ll have to do a lot of work to get back to where you used to be. Our brains work the same way, and without practice your staff may have difficulty recognizing phishing attempts.
Maintaining the programme isn’t just for keeping your employees sharp though. It’s also a way for you to teach your staff about new phishing methods and to make sure all new employees have been trained just as well as the rest of your staff.
To sum it up, continuous testing is the best way to prepare your staff to respond to a real phishing scenario.
Use the data you collect to improve your training methods
The data you collect from these phishing tests will be a valuable tool to guide your IT security practices. The data you should collect from every campaign is:
-
Number of people who clicked the link
-
Number of people who completed the requested action (for example, shared personal information)
-
Number of people who reported the email correctly
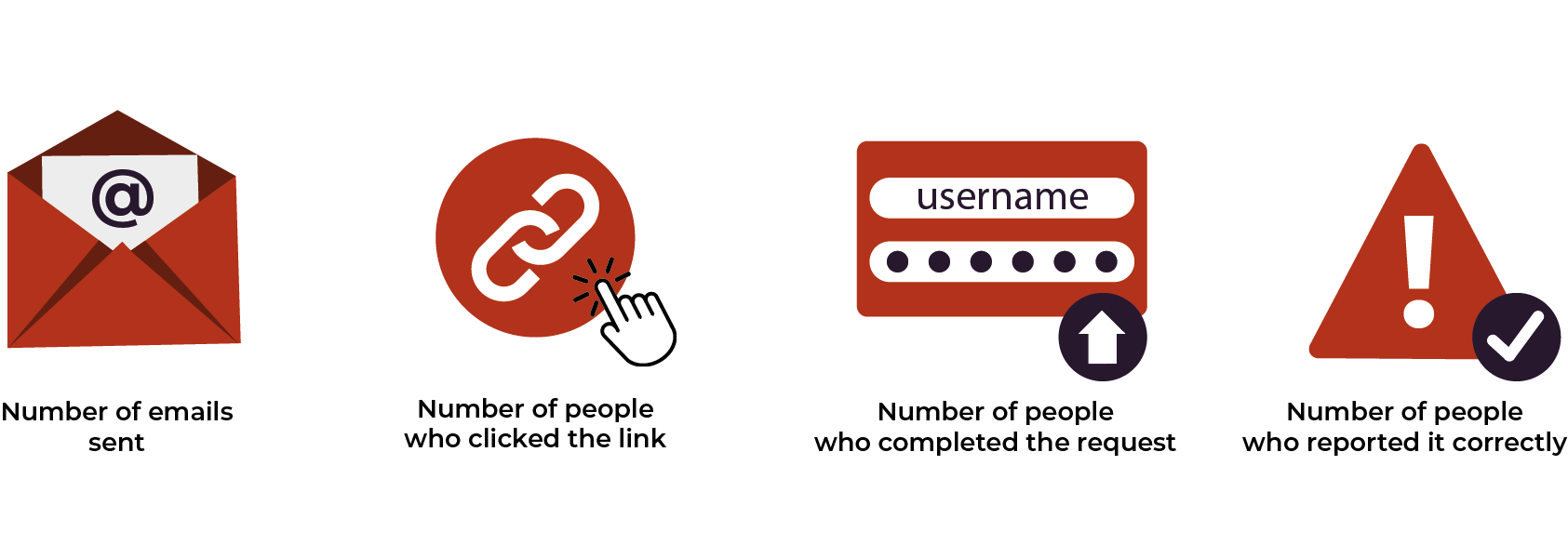
With this information, you can begin recognizing patterns. For example, the data can be used to:
-
Direct further awareness training topics
-
Determine how well employees understand your internal reporting policies
-
Focus additional training on the individuals who would benefit the most
Consider working with an external partner
Because successful phishing testing needs to be ongoing, it can take a lot of time to keep the programme going. This is one reason it might make sense to work with an external training provider. Partnering with a training provider can save you time when it comes to writing the test emails, administering the training, and analyzing the results.
Our phishing training does just that. We create and send simulated phishing emails to your employees, but you remain a part of the process with access to a live tracking platform and curated insights into how different teams perform. If you are interested in learning more, please do not hesitate to reach out to us.
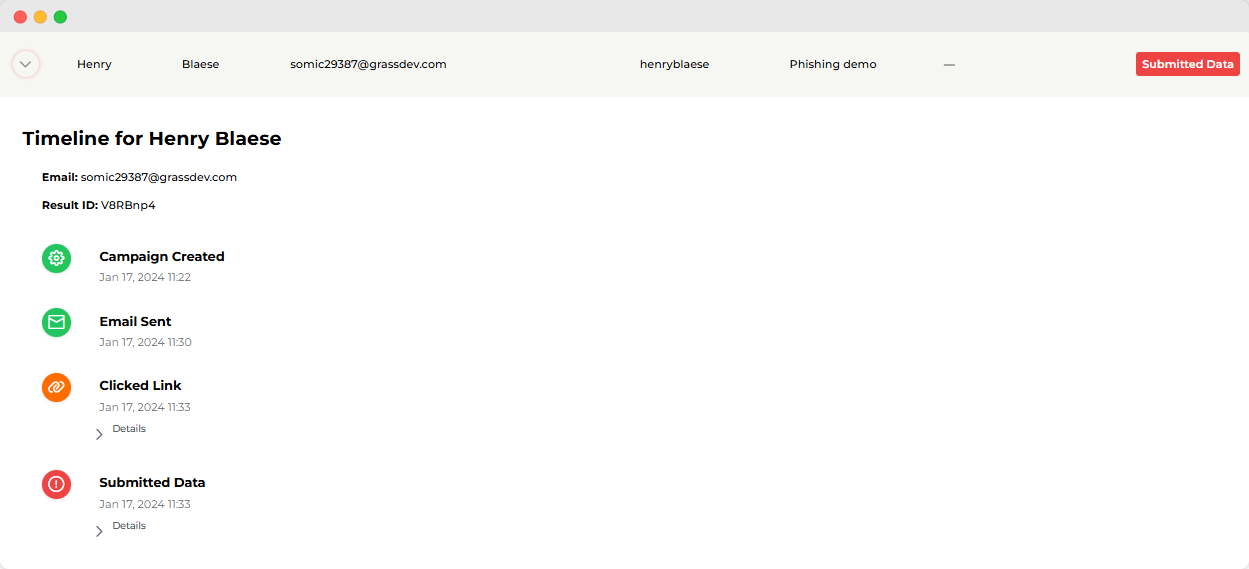
(Here's an example of how you can track results in detail from a phishing campaign in our platform)
Compliment phishing testing with other awareness-raising activities
Phishing testing is an asset for your team, but it shouldn’t be all that you do! You can think of phishing simulations as one part of a larger security awareness programme. Like learning to drive a car, you can’t succeed without both theory and practice. Just like you need both classroom instruction and hours practicing on the road to become a good driver, you also need general awareness training and simulated practice to achieve a strong cyber security culture!
Our work with IT security shows us that an aware team is the most resilient to cyber-attacks, and that’s why it is important to maintain a strong cyber security culture within your organisation. Aside from phishing training, you should use other initiatives to improve IT security awareness within your company and train your employees to become your strongest defense.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.