
What is Barrel Phishing? Beware Of The Conversational Phish
Barrel phishing is a dangerous form of attack because of its conversational nature. In these phishing attacks, the victim unknowingly lowers their guard, making them more susceptible to the attack that will follow. Like other forms of phishing, it’s possible to protect yourself and your organisation – all it takes is knowledge of the different types of phishing and common signs to look out for. By increasing awareness and training your team, you can protect yourself and your organisation from barrel phishing.
What is barrel phishing?
Barrel phishing, also called “double-barrelling” or “double-barrel phishing” is a type of phishing that relies on a series of two emails to get the victim to take the desired action. While regular phishing attacks involve a cybercriminal sending their victim one malicious email, barrel phishing attacks occur when the cybercriminal sends their victim two emails. Usually, the first email simply establishes a relationship with the recipient. Then, the second email is where the phishing comes into play. Here, the attacker requests an action from their victim, such as accessing a malicious link or file. Essentially, the first email is designed to lower the victim’s guard and increase the likelihood that the victim will complete the action requested in the second email.
Example of a barrel phishing attack
Here is an example of what a barrel phishing attack might look like:
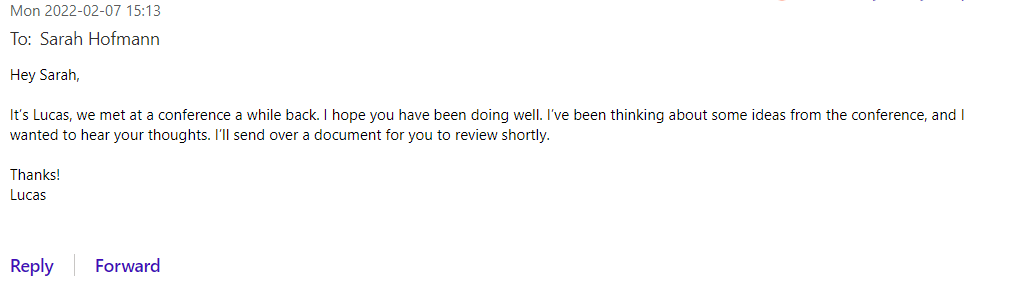
First email
Second email
Characteristics of barrel phishing emails
First email – builds trust and connection
As you can see in the example above, the first email in a barrel phishing attack is usually benign, meaning that it does not have many of the typical signs you would see in a phishing email. For example, there are no malicious links or attachments, and the sender hasn’t requested any kind of urgent action.
By claiming a vague connection to the recipient, the sender refers to a plausible social connection between them, which increases the recipient’s likelihood of reviewing the document when it’s sent. The email content is also designed to heighten the recipient’s curiosity: “Wow! Lucas remembers me from that conference we attended last year! And he’s been thinking of me and values my feedback!”
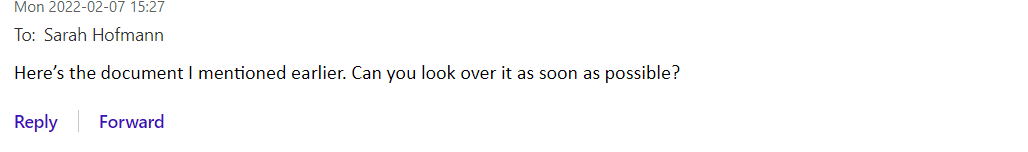
Second Email – includes malicious content
The second email is where the phishing takes place. It always has some kind of request, like asking the recipient to review an attachment in the example above. These emails may look like a traditional phishing email. For example, they typically have attachments or links and usually include a sense of urgency. But the first email lowers the recipient’s guard, so they usually aren’t looking out for the normal indications of a phishing email, like an unexpected attachment. In most cases, the second email does not come immediately after the first email. Usually, the attacker will wait an hour or so between emails so that their communication seems authentic.
The two emails work together to make a convincing phishing attack
Generally, the first email is designed to create a connection and might not even elicit a response. Like in the example above, it might set the stage for the second email, so that the recipient doesn’t question the attachment or link they have been sent.
The example above shows how the two emails work together to create a convincing phishing attempt. Without the first email from Lucas, the recipient would probably be suspicious of a random email with an urgent request to review an attachment. But the recipient’s guard has been lowered by Lucas’ first email. Before thinking twice, the recipient is likely to open the malicious attachment to see what Lucas sent.
Other examples of barrel phishing
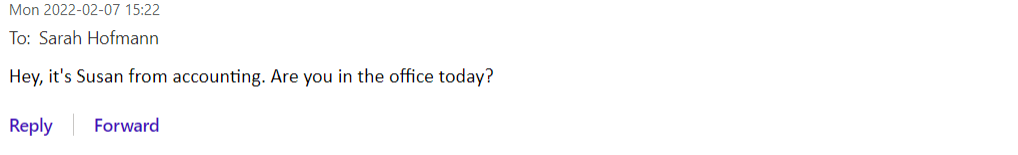
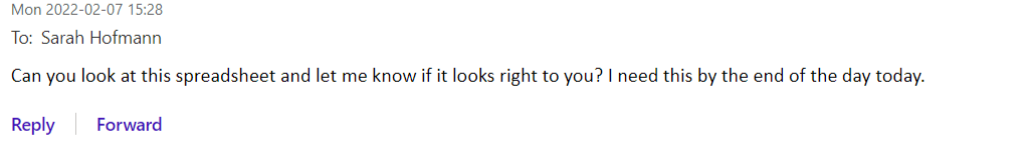
A common trend to look out for is a first email coming from somebody who could have a connection with you, followed by an email that asks something of you. Here are a few examples of what these emails may look like:
Example 1:
Email 1:
Email 2:
Example 2
Email 1:
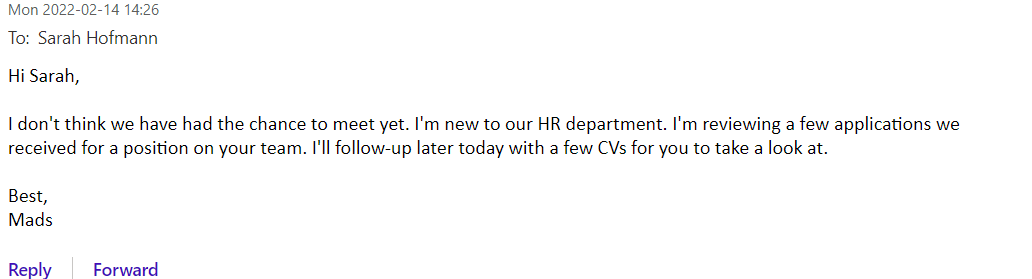
Email 2:
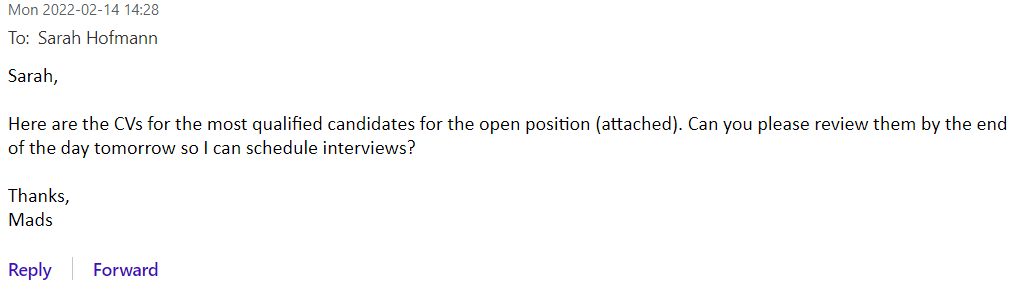
Example 3:
Email 1:
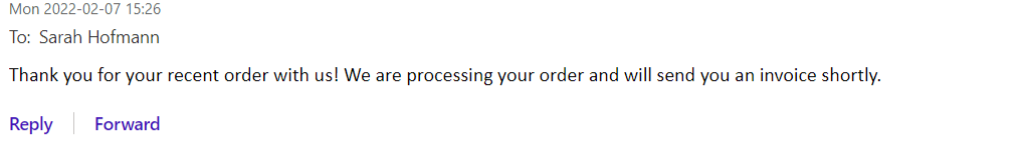
Email 2:
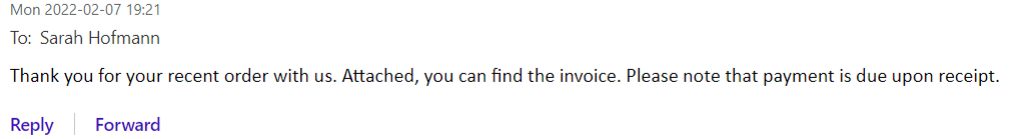
This last example shows how a cybercriminal could use barrel phishing to target both your personal and work email addresses. For example, the cybercriminal could do some open-source research on your company and pose as one of your company’s suppliers in this email exchange. The attacker could also send this series of messages to your personal email address by posing as a popular company whose services are widely used, e.g., PostNord, and hope that you recently used the company’s services.
Why is barrel phishing so dangerous?
The cybercriminals pretend to be somebody you know
The conversational nature of barrel phishing attacks means that the attacker usually poses as somebody that you either know or could have some connection to. For example, the attacker may impersonate a colleague or an extended friend. By pretending to be somebody on the fringe of your network, the attacker takes advantage of your sense of trust and curiosity. We’re more likely to trust people who share something in common with us, like working at the same company or knowing the same people.
To impersonate a colleague or somebody you may know, the cybercriminal has to do some research ahead of time to make their emails look believable. The attacker might be able to find an email address for your company online, and from there they rename their address to imitate that format. If you have never heard of the “colleague” who is emailing you, but their email address looks legitimate, you are likely to believe them.
You let your guard down without knowing it
Another reason barrel phishing is so dangerous is that these attacks lower the recipient’s guard without them realising it. Since the victim believes in a shared experience with the attacker, they are likely to ignore the signs of phishing that they would normally be alert to. Also, the combination of urgency with a believable context is something that victims are easily susceptible to. We are more afraid of disappointing somebody we are connected to than a random stranger.
The consequences of barrel phishing are similar to other phishing attacks
Since barrel phishing is a type of phishing, the consequences of completing the requested action are the same as with any phishing email. For example, if you open an attachment, you could unknowingly install malware onto your computer. Also, clicking a link and providing the information requested could result in the attacker getting access to personal or confidential information. Depending on the kind of information that is shared, the attacker could steal your identity or your money.
Regardless of the kind of information that the attacker gains access to, any exposure of personal data is damaging to the victim and their company.
How to protect yourself from barrel phishing
Evaluate all emails for signs of phishing
Protecting yourself from barrel phishing requires diligence and awareness. As mentioned earlier, several signs of a typical phishing email are usually present in the second email from the attacker, but these signs go unnoticed due to the connection that is established in the first email. Even if the email seems like it is coming from somebody you know, you should always look for common signs of a phishing email.
Pay attention to email addresses, links and your instinct
Check the email address itself, including both the name that appears with the address and the address itself. If the emailer claims to work at your company, but their email address or signature format is different from what your company uses, take caution. If the emailer says they work at your company, but you don’t know them, you could try searching for them in your company directory if you have one. In some cases, the attacker may pose as a company you do business with. If the request is abnormal or unexpected, you can contact a trusted person at that company or their general phone line.
You can also hover over links to see the true website they are directing to. If the website and the linked text don’t correspond, that is another sign to be cautious.
Finally, if the request is unexpected or gives you a weird feeling, don’t interact with the email until you can verify its authenticity. Contact the sender through a different channel to verify their request.
Educate for awareness
The most important step you can take to protect yourself and your organisation from these attacks is to create awareness. An aware team is more likely to recognize the signs of various attacks and take the appropriate action. Phishing testing is a great way to teach your employees to recognize all the different types of phishing, so they are prepared to detect even more complex attacks. In addition to standard phishing simulations, it’s important to train your team to recognise the most common types phishing attacks, so they are prepared to detect phishing in their own inboxes.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.


.png?length=800&name=EP17_%20The%208%20tells%20of%20a%20phishing%20email%20you%20and%20your%20colleagues%20should%20know%20-%20or%20else...%20%20(1).png)



