Every minute $ 17,700 is lost to phishing attacks. Phishing is a major challenge for organisations of all sizes. And it's no wonder - phishing is an effective way for cybercriminals to steal information and gain access to systems. In this blog post, I'll take you through the best practice for preventing phishing attacks to make sure your employees don't take the bait. I'll also run through the different types of phishing attacks that you and your employees need to know about. So, let's get started!
Why your employees are receiving phishing emails in the first place
Phishing attacks account for over 80% of reported security incidents and over the years, phishing emails have evolved dramatically. With new AI tools, phishing has become more sophisticated and harder to detect than ever before.
We confirmed this by having ChatGPT create a sophisticated phishing email for us. Take a look at how that went here!
Cybercriminals use phishing for accessing account credentials, commitng fraud and launching malware attacks.
Here are some more reasons for why cybercriminals are phishing your business:
- To steal valuable or sensitive information. That can be used to commit fraud or to launch a ransomware attack.
Most organisations don't invest enough resources in the human side of cybersecurity. This is essentially why phishing emails work. The good news is that there are ways to combat phishing. By increasing your employees' awareness and knowledge of phishing, you can prevent phishing emails from damaging your business. Let's look at that next!
How to protect your employees from falling for phishing attacks
Now that you know why you are receiving phishing emails, let's look at what you do to prevent phishing attacks from damaging your organisation.
The first thing you need to know is that everyone in your organisation has a role to play in creating a strong phishing defense. This means that all of your employees need to be aware of the risks and understand their own responsibilities in preventing phishing attacks.
So, now that we have that out of the way. Let's look at what you can do to make sure your employees have the right skills and knowledge!
Step 1. Educating your employees in cybersecurity awareness
Cybercriminals know how to make their scams look real and how to use human emotions to get employees to take the actions they want.
Security awareness training ensures that your employees are aware of common risks and threats. This includes how to identify a phishing email from a legitimate one. It's also important that your employees know what to do when receiving a phishing email. As warning other employees and reporting potential scams is essential for preventing another employee from falling for the scam.
I won't go into all the details of what to include in a security awareness program. But you are welcome to check out our full guide to creating your own phishing and social engineering training program here.
Step. 2 Training your employees to recognize different types of phishing attacks
Knowing about the most common phishing methods and the techniques behind them will help your colleagues recognize when and how they are being tricked.
Sophisticated phishing emails are often tailored to target a specific company or employee. Phishing emails range from relatively low-tech to highly researched and tailored campaigns.
Three different types of phishing attacks that use sophisticated techniques are spear phishing, CEO scams and whaling.
Here's why and how they work:
Spear phishing: Tailoring phishing campaigns to your organisation
Spear phishing is a phishing method where cybercriminals target and impersonate specific people in an organisation.
Targeted phishing emails are designed to manipulate behavior, exploiting the emotions and mistakes that make us human by using social engineering techniques. For example, you may be promised a gift card as the first person to complete a certain action, or the email may contain a short deadline or a false sense of urgency.
Deadlines or urgency increase the rate of data submission by 60%, so it's important to think twice and not be rushed into action by an email. Read more about how to spot the signs of a spear phishing e-mail here.
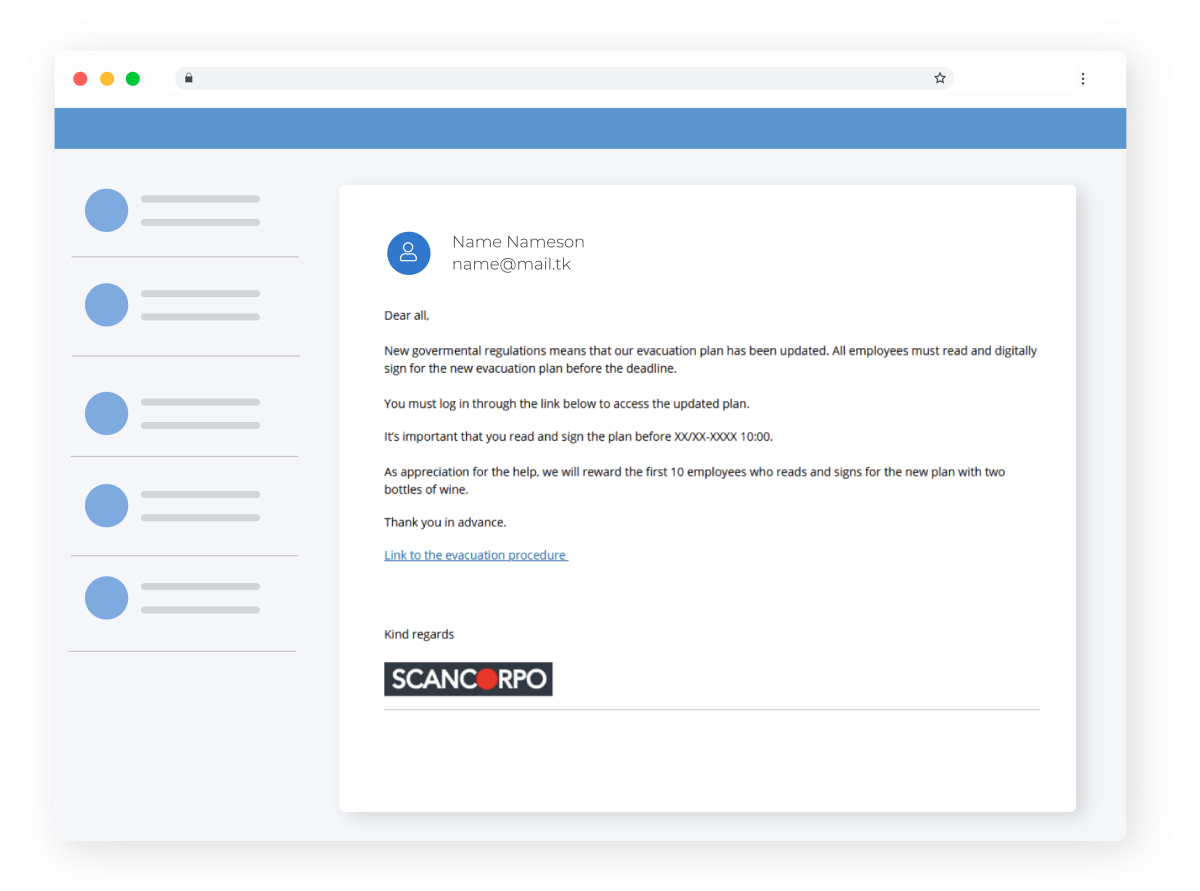
Example of phishing email using urgency
Whaling: Phishing emails targeting those in power
Whaling is a type of phishing email targeting CEOs and senior executives. The email is designed to trick the CEO by posing as an employee, client, or partner. Whaling targets are carefully selected, and based on extensive research into the person and the organisation.
By targeting those in power, fewer people are involved in the process and it’s more likely that the scam will go unnoticed. For example, a whale phishing email may contain an invoice from a supplier that only the CEO would oversee before making the transaction.
To be prepared for these types of attacks, CEOs and senior executives should be aware of the signs of whaling and know how to respond to an attack.
CEO fraud: Cybercriminals impersonating a senior executive
Who the sender is plays a vital role in how and when we react to emails, especially if that person is someone high up in the organisation. CEO fraud is a phishing technique where cybercriminals impersonate a CEO, or other senior member of the organisation.
This method relies on the persuasive power of authority and on employees “doing as they are told” without questioning those higher up in the organisation. Data from our own phishing campaigns shows that exploiting corporate authority is the easiest way to trick employees.
CEO fraud can have serious financial and reputational consequences. In the UK cases of CEO fraud have increased by 29 %, with losses set to continue rising. To protect your organisation from CEO fraud, your employees' ability to recognize and respond appropriately is your best defence.
Step 3. Using simulated phishing attacks to practice identifying phishing emails
The Danish Centre for Cyber Security recently found that 70% of untrained users are susceptible to spear phishing attacks. While most of us are confident in spotting phishing emails promising a free trip around the world, many struggle to spot the spear phishing, whaling and CEO fraud emails I just mentioned.
Sending simulated phishing emails is a hands-on way to train employees to recognize and take the right action against all types of attacks.

Receiving simulated emails, and even falling for them, will make employees realize the importance of training and how easy it is to fall for phishing emails if you are not vigilant.
Find our top tips for creating your own simulated phishing emails here.
Sending out fake phishing emails can also reveal if your employees know how to report a real phishing attempt. If you send out a fake phishing email and you are not getting the results you hoped for, you might need to give your employees more training on how to report phishing emails and make it easy for them to do so.
Step 4. Making IT security part of your company culture
The last tip I want to give you is to make cybersecurity more visible and talked about in your organisation.
To make cybersecurity part of your company culture, we recommend using a variety of learning materials and talking about cybersecurity as often as possible.
In addition to training sessions and simulated phishing emails, set aside time for questions during meetings or hang up themed posters around the office to remind people about cybersecurity. You can also organise regular cybersecurity discussions. This will not only remind your employees of the risks, but also encourage them to ask questions and talk to each other about cybersecurity.
These awareness posters act as a fun reminder while encouraging discussion about cybersecurity issues.
Preventing phishing attacks is a shared responsibility
Protecting your organisation is a shared responsibility, and all employees need to know how to recognize and respond to different types of phishing emails. Employees are often seen as the weakest link in an organization's phishing defense. But employees can be your strongest asset if you equip them with the right knowledge and training.
Read this blog post for more information on how to create awareness training that your employees will love!

