
Should You Phish Your Colleagues? We Think So!
Phishing testing, also called phishing simulations or phishing training, is a way to test how well your colleagues can detect a phishing email. Making the decision to start phishing testing for your employees can be complicated because it involves intentionally misleading others. When it’s done well, it has a really positive impact on your security. But if it’s done poorly, it can have negative consequences. In this post, we go over some of the benefits of phishing testing, what could go wrong, and share how phishing testing has improved the security of one of our customers.
Here you can read about
- Arguments against sending phishing tests
- Example of a phishing simulation gone wrong: FGU Vestegnen
- What’s the verdict?
- What our customer thinks about phishing testing
- Train your employees to recognize phishing emails today
Why would you phish your own staff?
Doing phishing testing in your office is a proven way to train your colleagues to detect malicious emails and take the correct action when they receive one. If you are already running an IT security or awareness training program in your office, phishing tests are a great way for your colleagues to put everything they’ve learned into practice in a real-life scenario. In this way, it serves as a natural complement to any training you’re already doing.
You probably also have a few colleagues who think that IT security isn’t a big deal, or that they would never fall for a phishing attempt. Phishing simulations are useful because they show your colleagues how difficult it can be to spot a phishing email. Maybe these colleagues will be a little more motivated to learn about IT security in the end.
Training your coworkers to recognize phishing emails
We learn best by doing. Sure, it’s one thing to read a poster about the signs of a phishing email, but nothing quite compares to the real thing. And while your colleagues are probably well versed in the phishing emails that come to their personal inboxes from criminals pretending to be a bank or fashion retailer, they might have a harder time detecting a well-researched spear phishing or CEO fraud email. Sending your staff these kinds of phishing test emails helps them broaden their awareness about phishing, which makes your organisation more secure.
Testing if your colleagues know who to report phishing attempts to
Your organisation should have clear instructions that people can follow if they receive a suspicious email. For example, a good reporting process could be to first tell the person in charge of IT security, and then warn your colleagues about the email.
The reporting process only works if it’s actually used. A fake phishing email is a way to test how well your staff understand the reporting process and whether they use it. The results can tell you if you need to have a simpler process in place or if people need a reminder about who to tell.
Preparing for a real-life attack
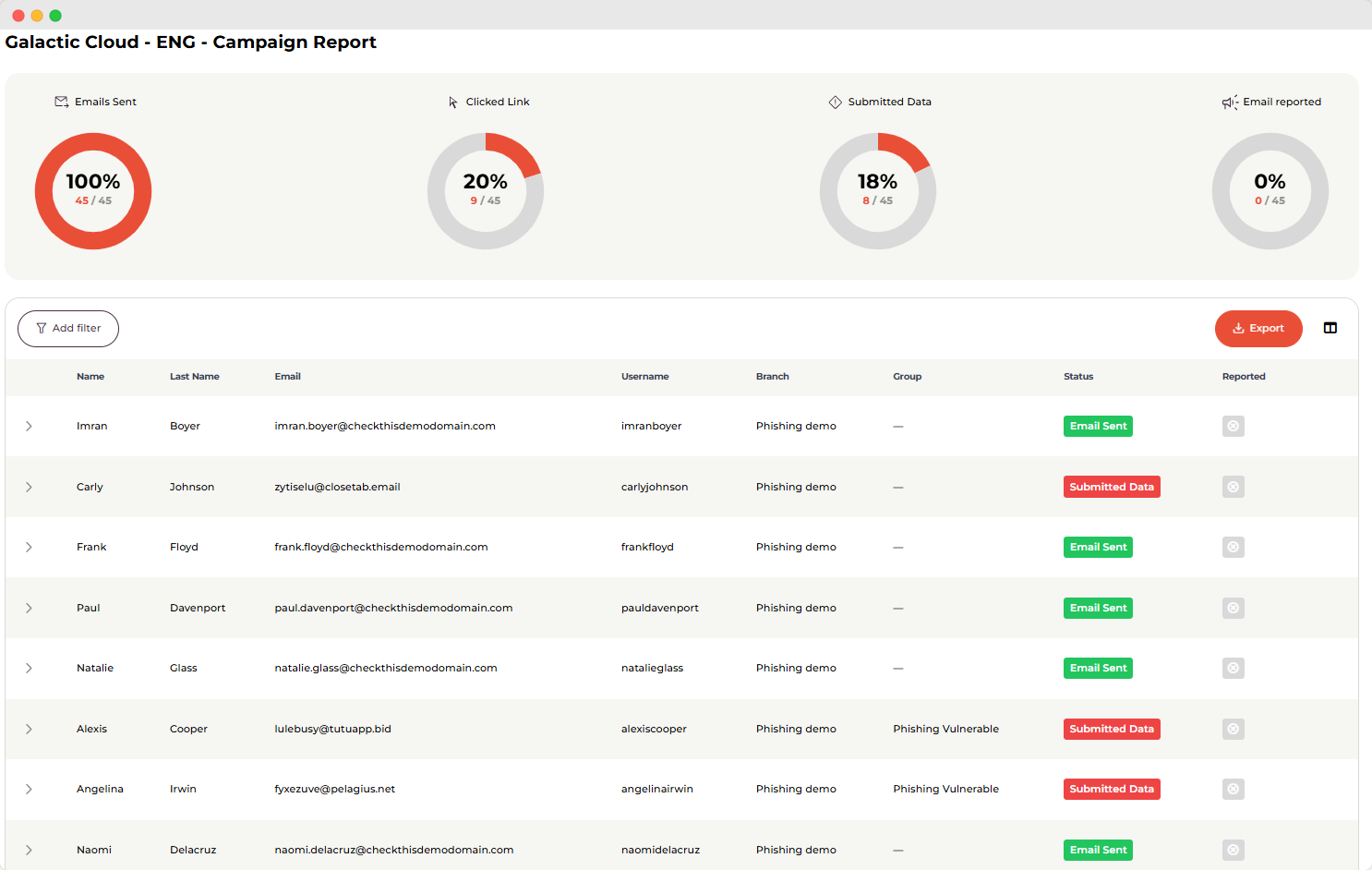
Our research shows that after continuous awareness training and phishing testing, users had at least a 50% reduction in mistakes made during phishing simulations. In our phishing testing, during the first phishing test, an average of 15% of recipients submit the personal information requested by the “cybercriminal.” By the third phishing test, that number goes down to only 6% of employees.
 This means that our users are much better prepared to handle a real-life phishing attack, and they’re less likely to click on links or submit sensitive information. You really can’t be too secure or overprepared because phishing is the biggest cybersecurity threat to organisations.
This means that our users are much better prepared to handle a real-life phishing attack, and they’re less likely to click on links or submit sensitive information. You really can’t be too secure or overprepared because phishing is the biggest cybersecurity threat to organisations.
Evaluating how well you have educated your coworkers about IT threats
The phishing test is not just a test for your colleagues. It’s also an evaluation of how well you have educated them about phishing and IT security. If a lot of people fall for the phishing test, it’s not necessarily a sign that they are doomed – they just need to know the material better. And we all know that test results measure both the quality of the teacher and the intelligence of the student. Good training is not supposed to be a “gotcha” moment, but a learning opportunity for both the teacher and the students.
So, phishing testing seems to have many benefits. What could be the downside? Some people are worried about starting phishing testing because of how their colleagues will react to being tested. We’ll cover these fears in the next part.
Arguments against sending phishing tests
The main reasons people are hesitant to start phishing testing is because they think it could be seen negatively by their colleagues. In this section, we’ll talk about why this fear exists and how you can avoid any hard feelings.
Unethical
Sending a phishing test can be seen as unethical because you’re deceiving your colleagues by putting their detection skills to the test. The lies you tell in the phishing email should be convincing and juicy, because the email content has to make an employee want to act. Phishing emails usually take advantage of the receiver’s emotions, so they could make a threat or create a sense of false urgency. All of these feelings can make your colleagues feel uncomfortable, which is why phishing testing can be viewed as unethical.
But these feelings will be brought on by any phishing email – whether it’s sent by the friendly IT team or a real cybercriminal. So, we believe it’s best to train your team to become familiar with these feelings (in a safe environment) so they are prepared when the real thing happens.
Loss of trust
Similarly, some fear that phishing testing could lessen the trust between the IT team and their colleagues. This could result from colleagues feeling that they were betrayed or misled unfairly. However, this is unlikely to occur if the goal of the training is clearly communicated and nobody is singled out for their performance. Sure, it would be easy to create distrust if John were called out in front of the entire office because he submitted his credit card information in response to a fake phishing email. It makes sense that he would feel betrayed and upset if he were humiliated in front of everyone.
On the other hand, done well, phishing testing can build trust between colleagues and the IT team. When colleagues see that results are only discussed at the company-performance level and that the IT team is invested in their learning, this can build trust.
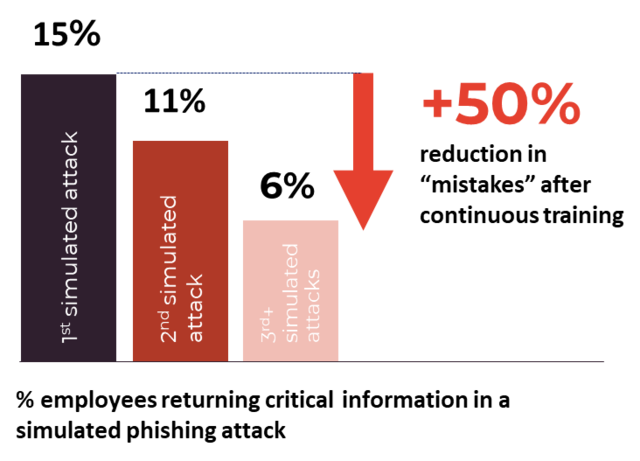
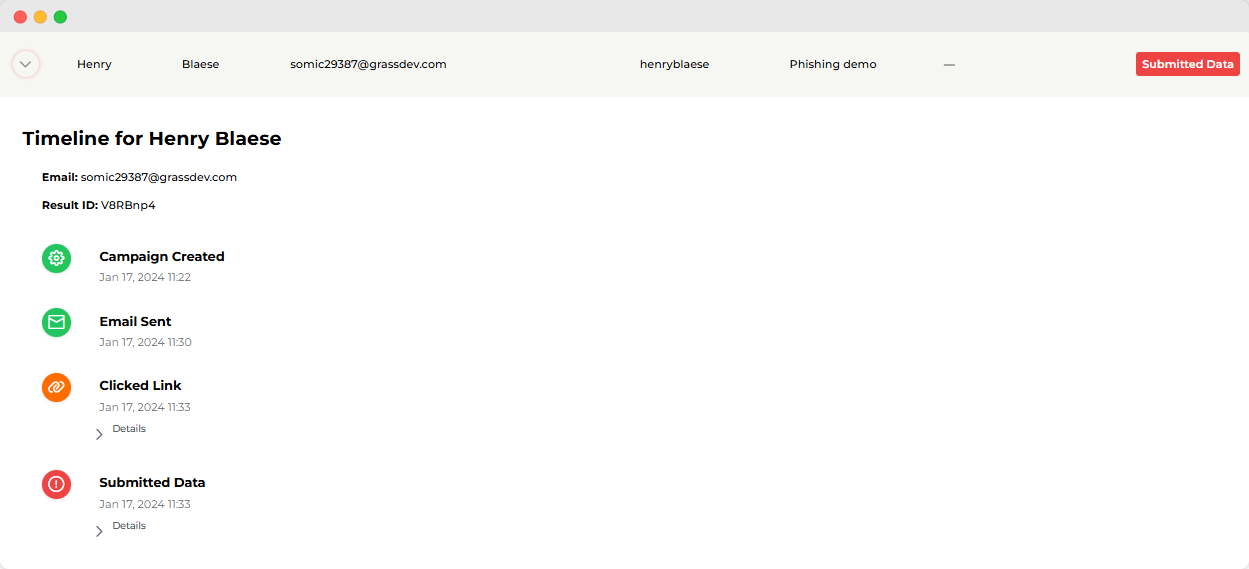 (example from our app where you see if individuals click)
(example from our app where you see if individuals click)
The solution: Good communication
Both of these potential issues can be resolved by communicating well about the goal of the phishing tests. Employees may fear that they will be judged or called out if they perform poorly. Communicating about the purpose of the training and how the results will be used/shared can ease these tensions before they appear. Make sure your colleagues know that it’s a learning exercise for everyone, including the IT team.
It’s also a good idea to stress that individual results won’t be shared company-wide, and that nobody’s job is at risk. Highlight that you are interested in how well the company overall performs, instead of looking at individual results. Once your colleagues know this, they’ll feel much more comfortable with the tests. We discuss this, and some other tips for creating a successful phishing testing program in this blog post.
Next, we turn to a case where a phishing test had negative consequences. FGU Vestegnen made the news due to a phishing test that their employees thought was unethical. Keep reading to see what happened.
Example of a phishing simulation gone wrong: FGU Vestegnen
FGU Vestegnen is an education institution in Denmark. In 2021, they sent out a phishing email to their employees that made the news because their staff reacted poorly. The phishing test email claimed that they received a donation of DKK 25 million as a reward for the organisation’s great work. The money would be divided between all the employees, meaning that everyone would get DKK 8,500. That sum of money would be theirs, with the simple request that they fill in their personal information.
When employees found out that it was a phishing test, and that they were not going to be DKK 8,500 richer, they were angry and disappointed. Among the criticisms was the fact that the email promised a bonus payment for good work, during a time when work conditions and pay were sensitive topics. Additionally, the email referenced a donation from an external foundation, which goes against some IT security companies’ codes of ethics.
The IT director of FGU Denmark originally defended the email, claiming that phishing tests should be attractive and realistic in order to be effective. However, the company has since apologized and suggested that they will find other ways to test phishing preparedness.
What went wrong here?
We can learn from the mistakes made by FGU. Where their phishing test went wrong was that it mentioned funds from a real external foundation, and it touched on a sensitive topic: work conditions. Pay and conditions at work can be sensitive topics for some employees, and that’s why you need to be careful when you design the content in your phishing emails. If you need some help thinking about what to write in your phishing emails, we have four sample campaigns that you can take a look at.
The case shows that it wasn’t the phishing test itself that was the problem, but rather the content in the email and how it was communicated. These two things, content and communication, are completely within your control, which means that you can do phishing simulations without having negative consequences.
What’s the verdict?
If you’re worried after reading about that poorly received phishing email, here’s where we can tell you that it’s all okay.
We think you should phish your friends, and it’s not just something we say or sell – we do it ourselves as well.
Go ahead and phish your friends
The benefits outweigh the potential consequences. And you can take steps to avoid negative outcomes or bad reactions. For example, telling your office that you’re going to start sending phishing tests before you send any out can solve the problem of trust issues arising.
Telling everyone about phishing testing beforehand can sometimes give you skewed results for your first phishing test, because employees may be more aware or primed to find a phishing email. So, it’s up to you to weigh the options and how you think your staff will respond to knowing they’ve been phished.
But use common sense
In many cases, staff are eager to learn and test their phishing detection skills. As long as you don’t publicly name and shame people who fall for the phishing trap, phishing tests are usually not a cause for unrest. Instead, you can share the results of the phishing test on a general level, for example, sharing what percentage of the company clicked on the “malicious” link and what percentage of people sent all of the requested personal details. Sharing the results on a general level can bring your organisation closer together by giving everyone a common goal to work towards.
We practice what we preach
We don’t just tell everyone else to phish their own employees while we shy away from it ourselves. We use phishing testing ourselves, in addition to awareness training, to keep our staff sharp and prepared to handle common IT security threats.
Here’s what our CEO, Rasmus Vinge, says about the phishing tests that we do internally:
"I see a big value in phishing training. I see that every time we send phishing mails to our team it becomes a talking point. This means that phishing becomes a part of the daily agenda and that people warn each other when they spot a phishing email which is ideally what we want. At the same time, we also see how many people fall victim to e-mails which can help us evaluate how good we've been at creating awareness ongoing and if we have to increase the level of initiatives."
We hear common stories from our customers, too, which is what you can read about next.
What our customer thinks about phishing testing
Our customer, DTU Biosustain, shares how phishing testing has improved their security. They use both our awareness training and phishing testing services, and their head of IT, Mads, thinks it has made their security stronger in many ways. For example, Mads says that:
-
Phishing testing is a good complement to other IT training activities
-
Phishing testing can help you see the baseline of how effective your other training activities are
-
Phishing testing gives you a real number of how your company is progressing and how well your colleagues can spot phishing emails
So, you don’t just have to take our word for it. Phishing testing works and can become an important part of your IT security work.

Train your employees to recognize phishing emails today
Phishing is the biggest security threat that companies face today, and it just takes one employee to fall for a phishing email for your business to be seriously interrupted. Plus, experiencing a breach that starts with a phishing email is extremely costly to any organisation.
If you want to learn more about phishing testing, you can use this form to book a free demo with one of our phishing experts. You can also check out this example of a phishing campaign with information about how many people clicked on the email and sent away their personal details. We look forward to hearing from you!
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.


.png?length=800&name=EP17_%20The%208%20tells%20of%20a%20phishing%20email%20you%20and%20your%20colleagues%20should%20know%20-%20or%20else...%20%20(1).png)



