A 2021 Cyber-Attack Has Sparked Positive Changes For Kalundborg Utility
In August of 2021, Kalundborg Utility received an unsettling message on their computer screens. All of their files had been stolen and encrypted. The hackers were demanding money in exchange for giving back the files. Fortunately, Kalundborg Utility managed to get the hackers out of their IT-systems without paying a single cent. Even before the cyber-attack, IT-security was already an important topic at Kalundborg Utility, but ever since the attack awareness has reached new heights. We spoke with Kim from Kalundborg Utility, on how they ensure that all employees are focused on security in their day-to-day work and how they best ensure that there will not be another attack.
| About Kalundborg Utility |
|
Kalundborg Utility supplies households with drinking water and distribute district heating in the town of Kalundborg, as well as cleaning wastewater from all of Kalundborg municipality. They also supply overflow water to some of the large organisations in Kalundborg. |
About Kim
Kim Breiner Ottobrøker
Compliancespecialist
Cand.Scient.Pol Copenhagen UniversityKim is responsible for GDPR and cyber security at Kalundborg Utility. He holds a master’s degree from Copenhagen University and is also a graduate from the Danish School of Media and Journalism. Communication takes up a good part of his work as Compliance Specialist, as this is an important part of spreading awareness. To put it simply, Kim is bridging into IT as he always differentiates between
‘[…] IT and cyber security. IT security is a lot of hardware whilst cyber security is softer. I work closely with IT people but the cyber part, the part of creating awareness, is only me.’
In this article Kim tells us about the cyber-attack Kalundborg Utility experienced in 2021. The article will also touch upon what they experienced and how Kalundborg Utility actively works with awareness training every day. Lastly, we will take a look at Kim’s specific advice for other companies, as well as the initiatives Kalundborg Utility has taken in their fight against attacks.
Happy reading.
Table of contents
- Attacked due to a bad VPN connection
- Openness is the key to good IT security
- A change in culture starts in the dialogue amongst employees
- After the attack
- Security initiatives are collaborative
- Changes following the hacking attack
- Three good pieces of advice for other organisations
- Create a good IT security culture in your organisation
Attacked due to a bad VPN connection
The attack on Kalundborg Utility happened when a hacker got in via a computer. They first tried to hack their way in by brute-forcing passwords, but it was through a bad VPN connection that they managed to get access to their systems and conduct a ransomware attack, that locked all of Kalundborg Utility’s systems. With a ransomware attack your thoughts automatically goes to phishing but phishing wasn’t the culprit in this case. In reality, 95% of all attacks happen due to human errors, which means that this attack goes under the last 5%. Kim explains that the procedures and contingency plans that Kalundborg Utility had in place in case of an attack, worked as intended:
‘After 12 hours our most vital systems were back up and running and we could work on it from there. I thought that was quite fast.’
During an attack you won’t have access to your digital files or systems, so it’s important to store files on procedures offline. This was ultimately what led them to regain their systems and get the hacker kicked out of their systems.
To be up and running again after 12 hours is more the exception rather than the rule. It is a testament to Kalundborg Utility having good processes and plans in place. On average you are down between 7-21 days during a ransomware attack.
IT dealt with the technical part of getting back up and running, whilst Kim was in charge of both the internal and external communication so let us dive into how he did that.
Openness is the key to good IT security
From the beginning of the attack communication was the key focus for Kim.
They needed open communication for employees but also to the public.
‘From the beginning I’ve never toned down on how a policy of openness is really nice. It is simply because a hacker attack and especially a ransomware attack is connected with shame. It’s a taboo topic for a lot of companies. […] But you also never get over it if you don’t talk openly about it.’
That is why Kim decided to talk about the incident with Kalundborg Utility's employees, but also with the local area and national news media.
Openness with employees
The day of the attack Kalundborg Utility just happened to be having a staff meeting. Kim took advantage of this and used it to inform the employees of what had happened and what it meant for them and the company. This open line of communication has helped provide the employees a shared understanding of what it means to be experiencing a cyber-attack. It’s not just something the management and IT team worked on.
‘This attack has become a part of a shared cultural frame. The way in which we think cyber security and how openly we speak about it. It is a part of our story now and we are also making it a part of our future story.’
The attack is not only a part of Kalundborg Utility’s story. It has also become a part of the onboarding of new employees. Here, the attack becomes a story of why and how cyber security is an important part of everyday life. This way, the attack is turned into a strength, as it becomes a learning experience throughout the whole organisation.
Local openness
Kim also had a focus on how they communicated the attack to the town of Kalundborg, due to a very special reason:
‘First and foremost, there is an element in us being located in Kalundborg, which is not a large city. Therefore, it was especially important that we sent out the right story right away and instilled calmness in the individual employee. This was not their fault; it was an attack from the outside.’
By being ahead on the communication Kim could better manage the information that was being shared with the employees and the town. This also meant they could avoid false rumours more easily. The attack was not due to incompetence from neither the employees nor IT team, it could have happened to anyone. That story is important to get out there in order to talk openly about this type of attack.
Later the news also hit national news media, where Kim took the time to engage in dialogue.
A change in culture starts in the dialogue amongst employees
Having an open dialogue both internally and externally has contributed to a shared starting point and understanding of why IT security is important, which contributes to a better IT security culture. Communication is a key tool in creating openness, where people feel comfortable asking questions if there is anything they are unsure of.
However, communication cannot carry the burden alone when it comes to creating a culture. Because of this Kalundborg Utility is making use of different methods to train and develop the culture. Here, CyberPilot’s phishing campaigns and awareness training courses are a big help.
‘The phishing campaigns are great. It is an effortless way of keeping it going. You do not have to slack on it.’
Phishing campaigns help the employees to be aware in their everyday life and fosters a dialogue amongst the employees when they discover a potential phishing e-mail.
Kalundborg Utility also receives awareness training courses, but Kim doesn’t just dish out CyberPilot courses, he also follows up on them and thereby takes it one step further to change the workplace culture.
‘I do a presentation for people on our staff meetings. I put a message out on our internal message board every week, and if there is something more such as a threat, I share it immediately. There is always a dialogue going on between the colleagues, which leads to my important message, which is to de-taboo, because if we can talk about, then that is the biggest security you can get.’
According to Kim, a culture is created when people are talking internally about IT security and for this to succeed Kim has an ambitious strategy for the organisation's awareness training. This strategy entails that all employees must pass their awareness training. This does not always happen on the first try, but after a couple of reminders people become aware that they have to do the courses.
‘I am striving towards 100% completion of courses. For this I partially use the tools available from CyberPilot, to see if people complete these courses. The other part is that I am continuously communicating about cyber security.’
Following the attack awareness training has since become a large part of Kalundborg Utility’s everyday operations and there is an expectation within the organisation, that everyone completes the courses. According to Kim, the employees always manage to complete them.
Choice of strategy to avoid future attacks
Kalundborg Utility got through the attack due to a strong IT-team and open communication to the employees and the public. But how do they avoid being targeted again?
Avoiding attacks in the future comes down to speaking up and setting up a framework for how to work with GDPR and cyber security. In such a job Kim says that;
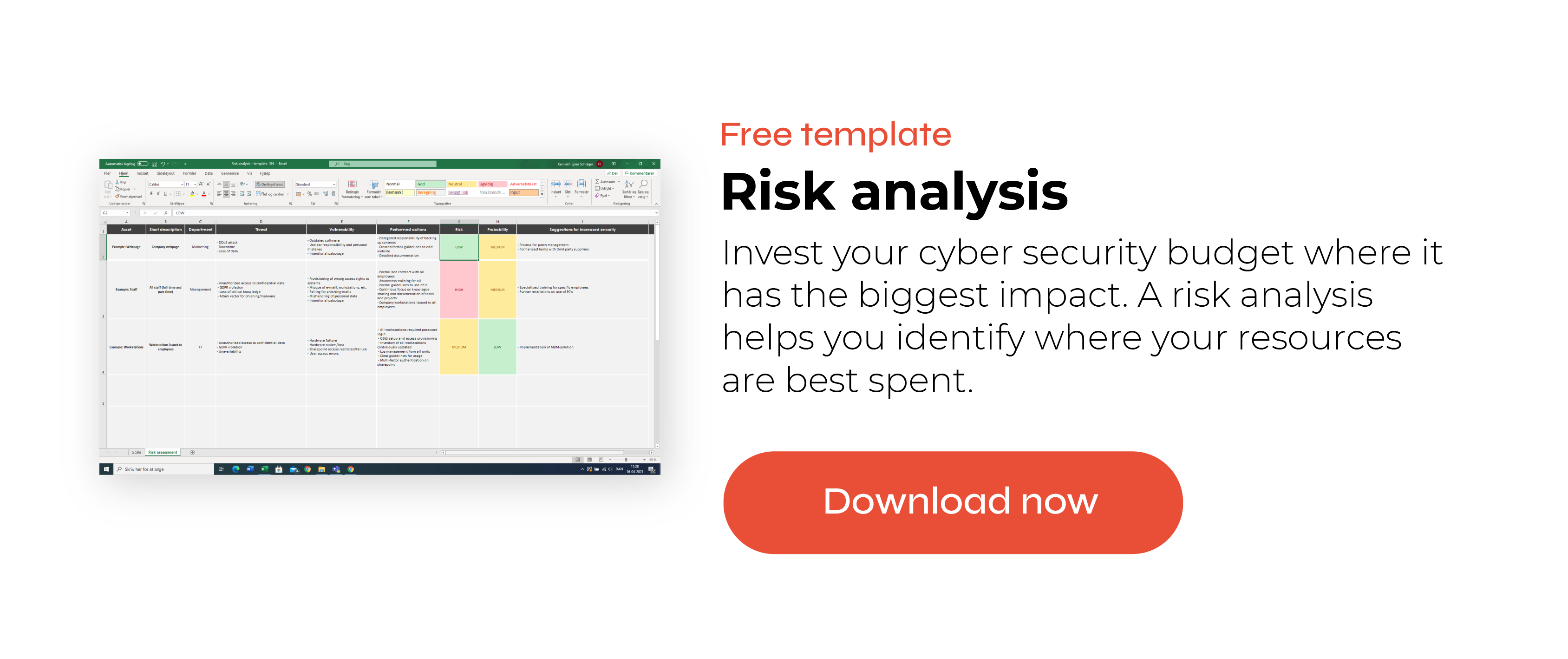
“Risk analyses are a super important part of cyber preparedness. Of course, it has to be based on IT systems, but you also have to make it on some of the softer parts. As previously mentioned, 95% of all mistakes are made by people.”
It’s not enough to just conduct a risk analysis on your IT assets. And that is precisely why focusing on that 95% takes up a lot of space for Kim in his compliance strategy:
“That is also the story I continuously try to get across to our employees, so they know that they are the weakest link in this chain. And there is no shame in that, it’s like this for everyone.”
It is okay to let the employee know that they are the weakest link, as long as they also know that that is completely okay and normal. Kalundborg Utility’s large focus on the employee has benefitted them. Kim’s colleagues have for instance criticised phishing campaigns for being too easy to spot. That could be an issue but that is precisely what Kim is happy about, as in his eyes that means the employees are thinking about what they are doing and clicking on. And it also shows that the phishing e-mail simulations actually work. He views the criticism as a symptom of Kalundborg Utility’s IT security culture being strong.
After the attack
How do you maintain a focus on both cyber security and GDPR?
Kim has obviously succeeded with creating awareness about the IT security at Kalundborg Utility, for instance by actively making use of the attack they experienced and creating a conversation in the organisation. It is, however, a continued challenge and is not limited to only cyber-attacks but also to GDPR.
“Well, GDPR is a different challenge. Cyber security, I think, moves along slowly but steadily, whilst GDPR in a lot of ways is about common sense and watching out for yourself in a digital world.”
Kim uses many initiatives to maintain both GDPR and cyber security. He does this by e.g., distributing courses, hosting introduction events for new employees and speaking about it in other contexts. He also switches it up, sometimes talking about GDPR an sometimes about cyber-security
Even though the two are interconnected Kim’s experience is that it can be difficult to get the IT cyber security culture to also include GDPR:
“Cyber security often centres around something external. GDPR often centres on how you yourself act and it is always easier to consider external factors, rather than looking inwards.”
Phishing, hackers, and outsiders are easier to communicate about, as it comes from the outside, us against them. But GDPR is a different challenge. Kim mentions that GDPR can be more difficult to implement correctly, as you often become blind towards what you are sitting in front of, which is why it needs to be addressed constantly:
“It must be addressed in a completely normal manner, where it is relatable. There are many ways. You also do it in your courses, […] it is important to peel away some of the legal stuff, because many people shut down when that is brought up.”
There often is a consensus on GDPR being a complex subject, but here Kim thinks that it’s important to talk it down, as it mostly is concerned with common sense. There needs to be a focus on common sense as opposed to the law behind it, but how does one do that?
CyberPilot helps talk down the topics
We know that it can be difficult to do everything all at once. Where to start and what to start with? Cyber security is a complex size, that Kim believes CyberPilot is helping with:
“It is actually kudos to you and your courses. I like that they are not long in length. I have previously been with companies, where a single course took 45 minutes to complete and by that time you have completely tapped out. In your courses you might take away 5 things, which you can remember. That is far more effective use of the employees’ time, as they will remember much more of the 5 minutes than the 45 minutes. In the real world that is very logical, but unfortunately many people are doing the opposite.”
Kalundborg Utility has decided that cyber security and GDPR is something they make use of and not something that just has to be checked off a list.
“If it were just something to be checked off, they would not need someone like me to keep people in line. Then they would just send it out and check it off. Nothing about following up on how many has completed and so on, but people do not learn from that.”
This led us to asking which other actions Kim has implemented in the company. Kim tells us that they have taken many concrete actions to strengthen the cyber security and become more GDPR compliant in Kalundborg Utility.
Security initiatives are collaborative
The three initiatives Kim tells us about has occurred in cooperation between CyberPilot and Kalundborg Utility.
Courses and the possibility for reading out the courses:
The first initiative concerns the different courses that CyberPilot offers and the voice-over feature that reads text aloud.
“Last year we had two employees with dyslexia, and they pointed out that the courses were a bit hard for them, because they also included some text. You then added some reading aloud or speak, so all the dyslexic employees could participate. […] It is a massive help for self-help, that there is a feature such as reading aloud. It is an important parameter that you must maintain.”
Reading aloud is an important initiative to creating a culture for the WHOLE organisation.
Phishing campaigns:
The second initiative Kim focuses on, we’ve already touched upon; the phishing campaigns.
“I started running these phishing campaigns a bit more structured, because they are a real eye-opener to people. It also gives me a tool to see if the things I do in my everyday operations are working. Now I have two measurements to relate to – one from last year and one from this year. Already now I can see that there is a very noticeable difference in the number of clicks.”
Phishing campaigns can both be used to create awareness among employees, but also to measure the effectiveness of one's initiatives.
Following up:
The third and last initiative is the following up after a course or a phishing campaign. This is super important for both starting the informal conversation about cyber security, but also to see the effectiveness of one’s campaigns. To this Kim says that if there’s no following up on the courses, he sees no learning:
“If the courses are sent out once a month and then you complete it. That is fine. Check off that. Moving on. Here, we try to articulate it and make it a part of our processes and our everyday. […] cause so much knowledge and time is lost if you do not follow up on it. Then it’s just another list of check marks.”
It’s important to not only view awareness training and phishing campaigns as something to be checked off. Following up on campaigns and training are what creates the dialogue in the organisation, and as mentioned earlier the dialogue is Kim’s most valuable tool to creating a cyber security culture.
Changes following the hacking attack
Following the hacking attack Kalundborg Utility experienced, the above-mentioned initiatives has been a change and improvement. Kim tells us that they were not focusing on training before the attack, whereas it’s now a part of their everyday.
“It is not just a course that is sent out once a month. If we are running phishing campaigns, there is also some debriefing for all employees, so they know that it has happened and what the results were. We also go over what one should have been aware of in the course or the e-mail and what to improve for next time.”
Aside from this, Kalundborg Utility has had the opportunity to register incidents, when the employees receive mysterious e-mails. This tool provides the opportunity to work statistically with phishing e-mails and to spot tendencies.
What does the employees think of the phishing e-mails?
We believe that all organisations should phish their employees. Phishing training is a way to test how good your colleagues are at spotting phishing e-mails, but it can be complicated to get started, as it is about intentional deceit of others. If done properly, it can have a huge positive impact on your safety, but if it is done wrong, it can have negative consequences and meet resistance from one’s colleagues.
Kim experienced several emotions from colleagues, when he sent out the first phishing e-mail, but the follow up on the e-mail created calm and understanding:
“The first time they were upset. There was no doubt. My phone was red hot the same day. […] The second time I did it, people took it with their chins up and a smile. For me it is important to get feedback as it is a tool for dialogue. This is a pressure test of the organisation. There wasn’t a single sour frown over it, the last time I sent one out. Because people can see why I do it.”
Kim believes that following up, informal conversations and debriefing is what creates the cyber security culture. Furthermore, his approach to phishing e-mails and the courses has created an openness in the organisation.
“Just the fact that they are not afraid of reaching out and saying that I have received this or clicked on something without it being connected to shame or a pointed finger. […] In reality, we are building trust in the form of being able to talk about it. That means people can start sharing knowledge across the organisation.”
Making cyber security a part of the organisational culture means they do not have to start over every time new employees join the organisation. As it is an integral part of the company.
Three good pieces of advice for other organisations
Finally, we asked Kim if he had three good pieces of advice that other organisations can use.
Get the management on board
Kim’s first advice is to get the management on board:
“First and foremost, it is about management having a focus on attacks and acknowledging that this is going to happen to us. […] It is not a question of if, but of when. If you take that on your shoulders and acknowledge it – then you are already well on your way.”
Without management having your back, it’s difficult to enforce initiatives.
De-taboo it
But how does one get the management in on it?
“That’s another point and that’s something I think is really important. I think that I’ve done a lot with de-tabooing it here. You have to talk about it.”
Here we’re back to the dialogue. Talk about why it’s important and what the weaknesses in the organisation are.
Culture change with routines
Kim thinks that it’s important that security doesn’t just become a check mark, but a culture change and an integrated part of your everyday in the organisation. It has to be routine.
“In reality it is only a symbol of two other things; articulation and management support. You will get nowhere with IT security unless management is aware of it and acknowledges their responsibility. That is what we have done here. There is a big focus on it from the management. This leads to it seeping down into the organisation.”
You have to speak openly about IT security in management, as well as board and executive board. A cultural change only happens if both the employee and management are aware of the risk and possibility of an attack.
Create a good IT security culture in your organisation
Kalundborg Utility has conducted many good initiatives to improve and secure the organisation against attacks. In the end this has functioned as a cultural change in the organisation. You can do as Kalundborg Utility has and secure your organisation against attacks. Start with our awareness training, where you can try 14 days free of charge.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.