
8 essential topics for awareness training
There's a lot of things you can cover in security awareness training. But here's 9 topics we think you should cover.
Psst: the image below is a bit outdated and lacking the topic numer 9. Read on to see what it is ;)
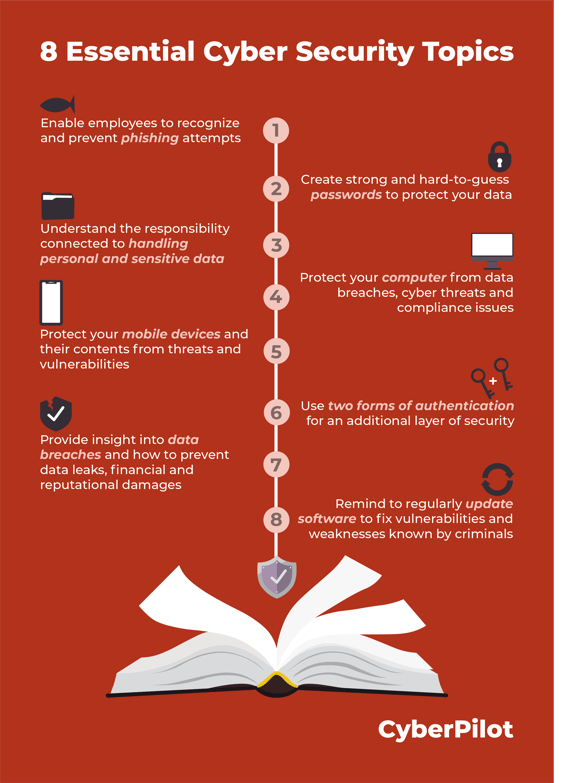
1. Phishing
Let's start off with one of the most important courses which is phishing awareness training, it teaches employees about recognizing and avoiding deceptive emails and messages crafted to trick them into giving away sensitive information, including passwords. The goal is to empower employees to be more cautious and vigilant to prevent falling victim to phishing attempts.
Key training elements for phishing awareness:
- Help employees recognize phishing emails and messages more easily by sharing real-life examples that illustrate common tactics used by cybercriminals.
- Highlight the importance of double-checking any unexpected messages.
- Emphasize the significance of not clicking on suspicious links or downloading unfamiliar files.
- Keep employees in the loop on new phishing tricks and trends by giving them regular updates.
2. Password best practices
Password security means keeping your passwords safe from unauthorized access. It involves creating strong, hard-to-guess passwords, not sharing them with others, and using additional security measures like Two-Factor Authentication (2FA) to protect your accounts and sensitive information.
Key training elements for password best practices:
- Instruct employees on crafting robust and hard-to-guess passwords.
- Emphasize the significance of password managers for securely storing and managing passwords.
- Introduce the concept of 2FA as an extra layer of security for their accounts.
3. Taking responsibility for personal data
Personal data, in the context of awareness training, refers to any information that can be used to identify an individual. This type of data can be directly associated with a specific person or used in combination with other information to identify an individual. It's essential for employees to understand what constitutes personal data and how to handle it in accordance with the GDPR.
Key training elements for handling personal data:
-
Provide training to employees on recognizing and managing personal data, including names, addresses, and financial information.
- Emphasize compliance with data protection regulations and the legal and financial consequences of non-compliance.
- Provide guidance on secure practices when dealing with and storing personal data, including encryption, access controls, and secure disposal methods.
- Remind employees to promptly report any breaches or mishandling of personal data.
4. Protect your work computer
Employees should know how to protect their work computers because they're the first line of defense against data breaches, cyber threats, and legal consequences. This understanding not only prevents internal issues and ensures compliance with data regulations but also reduces downtime, safeguards sensitive information, and lowers tech support costs.
Key training elements for how to protect your work computer:
- Ensure employees install only approved software to avoid security risks like viruses and breaches.
- Highlight the importance of keeping software and systems up to date to prevent cyber vulnerabilities.
- Share guidelines for secure online browsing and downloading practices.
(example of courses topics on our app)
5. Mobile device security
Mobile device security is the practice of protecting smartphones, tablets, and other devices from threats and vulnerabilities. It includes setting up security features like passwords, using secure Wi-Fi connections, and being cautious about app downloads. The goal is to ensure the safety of both the device itself and the data it contains, especially in case the device is lost or stolen.
Key elements for mobile device security training:
- Instruct employees on establishing robust passwords for their mobile devices to ensure the safety of their information.
- Emphasize the importance of using secure Wi-Fi connections, particularly in public spaces, to protect their online activities.
- Highlight the importance of installing apps exclusively from reputable sources to avoid harmful downloads.
6. Two-Factor Authentication
Two-Factor Authentication (2FA) is a security method that requires two forms of identification before granting access to an account or system. It adds an extra layer of security beyond just a password, making it significantly more challenging for unauthorized users to gain access to sensitive data.
Key elements for 2FA training:
- Raise employee awareness about the advantages of employing 2FA, including improved account security and defense against unauthorized access.
- Deliver comprehensive, clear, and concise step-by-step instructions in the training, guiding employees on enabling and using 2FA across various accounts and applications.
7. Security breaches
Security breaches refer to instances where unauthorized individuals gain access to confidential data, potentially resulting in data leaks, financial losses, and damage to an organization's reputation. Understanding security breaches and how to prevent them is crucial in maintaining data integrity.
Key training elements for security breaches:
- Provide insights into various security breaches, including data breaches, network intrusions, and social engineering attacks, ensuring a clear understanding of potential threats.
- Explain the steps to take in case of a security breach, including reporting the incident and minimizing further damage.
- Promote a secure culture by reminding everyone it's everyone's job to keep things safe. Encourage ongoing learning and staying alert to make your defenses stronger against possible issues.
8. Software updates
Regular software updates are crucial for maintaining the security and functionality of your computer systems and applications. Updates often include patches that fix known vulnerabilities, making it much more difficult for cybercriminals to exploit weaknesses in your software.
Key elements for software update training:
- Explain why updating software is essential for security and how it prevents potential breaches.
- Provide guidelines on how to check for and install software updates on various platforms and applications.
- Emphasize that all employees share the responsibility of ensuring their devices and software are regularly updated to minimize security risks.
9. AI and security
Artificial intelligence (AI) is becoming an increasingly common tool in the workplace, helping with everything from writing emails to analysing data. While AI can boost productivity and efficiency, it also introduces new security risks.
Employees must understand how to use AI tools responsibly, protect sensitive information, and recognise when AI-generated content might be used maliciously. Cybercriminals can exploit AI to create more convincing phishing emails, deepfakes, and automated attacks — making awareness and critical thinking more important than ever.
Recent research shows that as many as 77% of employees share sensitive company data via generative AI tools, creating serious compliance and data-loss risks.
Key training elements for AI and security:
-
Educate employees on how AI tools process and store data, and explain why sensitive or personal information should never be shared with them.
-
Highlight the ways AI can be misused by cybercriminals, such as generating fake messages, voices, or videos that seem authentic.
-
Encourage employees to verify the authenticity of suspicious or “too good to be true” content.
-
Provide clear company guidelines for safe AI use — including which tools are approved and how to handle data securely.
-
Promote critical thinking and a cautious mindset when interacting with AI-generated content, both in and outside of work.
Additional awareness training topics
Now that we've covered the essential awareness training topics that you should include in your cybersecurity training, we can move on to explore some valuable additional topics that can contribute to a well-rounded cybersecurity training program.
Social engineering
Social engineering is a form of manipulation where individuals, often cybercriminals, trick or deceive people into revealing sensitive information or performing actions they wouldn't normally do. It involves psychological manipulation and can take various forms, such as impersonating someone trustworthy or using convincing stories to gain trust and access to information or systems.
Key training elements for social engineering:
- Explore various social engineering tactics, including impersonation and pretexting, to enhance awareness and recognition.
- Urge employees to be cautious in situations where they may face social engineering tactics. Emphasize the need for skepticism and alertness.
- Highlight how crucial it is to confirm who is making requests. Encourage employees to follow verification steps to ensure that requests and inquiries are legitimate.
Secure remote work
Secure remote work involves ensuring that employees can work from outside the office while maintaining the same level of cybersecurity and data protection. It includes using VPNs for secure connections, creating a safe home office environment, and securing home Wi-Fi networks to prevent data breaches and maintain productivity.
Key training elements for secure remote work:
- Explain how to use Virtual Private Networks (VPNs) for secure internet connections when working remotely.
- Remind employees to avoid using public Wi-Fi while working away from the office.
- Share tips on creating a secure home office setup, and how to secure their home Wi-Fi networks to protect company data.
Ransomware
Ransomware is a malicious type of software that is designed to do harm. It works by encrypting a person's computer files or locking them out of their own computer. In simple terms, it's like having your important files put into a locked box that you can't open. Then, the cybercriminals behind the ransomware demand a ransom, to give you the "key" to unlock your files or computer. If you don't pay, they may keep your data locked, which can lead to losing important information, financial loss, and causing chaos in your work.
Key training elements for ransomware:
- Educate employees on recognizing ransomware warning signs, such as unexpected pop-ups and files suddenly becoming unreadable.
- Emphasize that employees should never pay ransoms. It's essential to discourage negotiations with cybercriminals.
- Stress the importance of reporting ransomware incidents promptly to the IT or security team for swift action.
- Provide guidelines for proactive steps like regular data backups, using reliable security software, and exercising caution with email attachments and links.
Shared responsibility for cybersecurity
When it comes to your company's cybersecurity training, it's important to stay updated and cover a wide range of topics. We've looked at the essentials to kick off awareness training, there's even more to explore in our complete course catalogue.
Every employee, whether they're tech-savvy or not, shares responsibility for your company's cybersecurity. They can't rely solely on the IT department to keep things safe. By including these key topics in your security awareness training program, you can empower your employees to become vigilant defenders against cyberattacks. Remember, cybersecurity is an ongoing effort, and regular training is essential. Invest in your employees' knowledge and awareness, and you'll significantly reduce the risks.
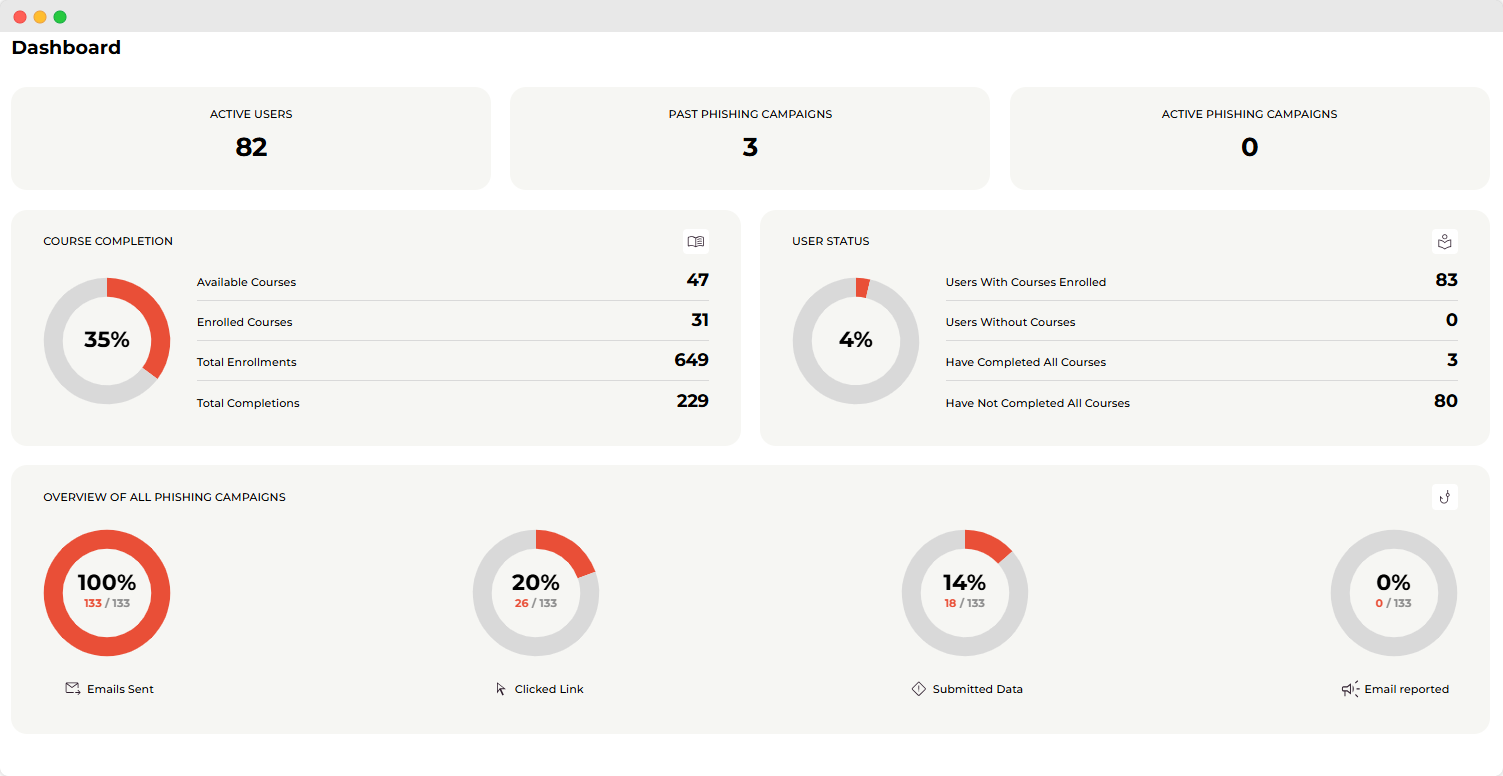
(example of dashboard on our app)




